11.6.1 Packet Tracer - Switch Security Configuration
Onlines
Mar 18, 2025 · 7 min read
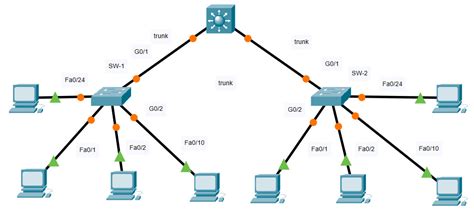
Table of Contents
11.6.1 Packet Tracer - Switch Security Configuration: A Comprehensive Guide
This comprehensive guide delves into the intricacies of switch security configuration using Packet Tracer, focusing on the specific requirements of 11.6.1. We'll explore various security mechanisms, their implementation, and best practices to fortify your network against common threats. Understanding these concepts is crucial for building robust and secure network infrastructures.
Understanding the Importance of Switch Security
Before diving into the specifics, let's establish why switch security is paramount. Switches operate at Layer 2 of the OSI model, controlling the flow of data within a local area network (LAN). A compromised switch can grant attackers complete access to your network, allowing them to eavesdrop on traffic, inject malicious code, and launch denial-of-service (DoS) attacks. Securing your switches is therefore a fundamental aspect of overall network security. This is especially true in the context of Packet Tracer simulations, which mirror real-world network scenarios and vulnerabilities.
Key Security Features in Packet Tracer (11.6.1)
Packet Tracer 11.6.1 provides a robust simulation environment to practice implementing various security features on network switches. These features include:
1. Secure Password Management
Strong passwords are the first line of defense. Avoid using easily guessable passwords, and leverage features such as password complexity requirements within Packet Tracer's switch configuration to enforce strong passwords. Regularly changing passwords is also critical. Packet Tracer allows you to configure password policies to ensure that administrators adhere to these best practices.
2. SSH Access
SSH (Secure Shell) provides a secure way to remotely manage and configure your switches. Unlike telnet, which transmits data in plain text, SSH encrypts all communication, protecting your credentials and configuration commands from eavesdropping. Within Packet Tracer, you can enable SSH and configure the port (usually port 22) and authentication mechanisms.
3. Access Control Lists (ACLs)
ACLs are powerful tools for controlling network access. They filter traffic based on various criteria, such as source and destination IP addresses, ports, and protocols. In Packet Tracer, you can configure ingress and egress ACLs on your switches to block unauthorized access to specific ports, devices, or network segments.
Example: Blocking unauthorized access to a specific server.
You might configure an ACL to deny all traffic destined for a server with IP address 192.168.1.100, effectively protecting it from external attacks. This example helps demonstrate the practical application of ACLs in a simulated environment.
4. Port Security
Port security helps prevent unauthorized devices from connecting to your network. It allows you to define which MAC addresses are permitted to connect to specific ports. If an unknown MAC address attempts to connect, the port is shut down or placed in a restricted mode. This is crucial for preventing MAC address spoofing attacks.
Example: Protecting a server port with port security.
By limiting access to a specific server port (e.g., a server connected to port 1) to only one MAC address (the server's MAC address), you prevent other devices from connecting and potentially compromising the server.
5. VLANs (Virtual LANs)
VLANs segment your network into smaller, logically isolated broadcast domains. This enhances security by restricting the broadcast scope and preventing unauthorized access between different segments. In Packet Tracer, you can create and configure VLANs on your switches, assigning ports to specific VLANs. This is a fundamental security measure for larger networks.
Example: Separating user traffic from server traffic.
You might create a separate VLAN for sensitive server traffic (VLAN 10) and another VLAN for user traffic (VLAN 20). This isolation prevents users from directly accessing servers, even if they somehow gain unauthorized access to the network.
6. STP (Spanning Tree Protocol)
STP prevents loops in your network topology, which can lead to broadcast storms and network instability. While not strictly a security feature, STP enhances the overall network resilience and stability, indirectly contributing to improved security by preventing these disruptive events. In Packet Tracer, you can configure STP to prevent loops and ensure redundancy while maintaining a secure network environment.
7. DHCP Snooping
DHCP snooping prevents unauthorized DHCP servers from providing IP addresses to your network clients. This stops rogue DHCP servers from distributing incorrect or malicious IP addresses, which is a vital aspect of security. In Packet Tracer, you can enable DHCP snooping on your switches to ensure only trusted DHCP servers can provide IP addresses.
8. Dynamic ARP Inspection (DAI)
DAI is a mechanism that validates ARP requests to prevent ARP poisoning attacks. ARP poisoning involves an attacker sending false ARP replies to redirect traffic intended for legitimate devices. DAI helps to verify that the source IP addresses in ARP packets belong to the MAC address they claim to possess. Implementing DAI within Packet Tracer enhances your switch security against ARP-related attacks.
9. Private VLANs
Private VLANs allow you to create isolated VLANs within a larger VLAN. This provides finer-grained control over network access and restricts communication between virtual LANs within the same physical VLAN. This level of segmentation adds another layer of protection to network resources.
Example: Isolating sensitive servers from other virtual machines.
Within a VLAN used for hosting virtual servers, private VLANs could segregate high-security servers from less secure ones, further protecting important data and services.
10. 802.1x Authentication
802.1x provides port-based network access control. This requires authentication from a client before granting access to the network. Implementing 802.1x with RADIUS servers in Packet Tracer ensures that only authenticated clients gain network access, preventing unauthorized users from connecting. This is a particularly robust form of network access control.
11. Monitoring and Logging
Regularly monitoring your switch logs is essential for detecting and responding to security incidents. Packet Tracer's logging capabilities allow you to record important events, such as login attempts, authentication failures, and ACL violations. Analyzing these logs helps identify potential threats and vulnerabilities.
Implementing Security Configurations in Packet Tracer
The specific steps for configuring these security features vary slightly depending on the switch model simulated in Packet Tracer. However, the general workflow usually involves accessing the switch's command-line interface (CLI) and using specific commands to enable and configure the security features.
Here is a generalized outline:
- Access the Switch CLI: Connect to the switch using a terminal emulator (like the one provided within Packet Tracer).
- Enable Privileged Mode: Use commands like "enable" or "en" to gain privileged access.
- Configure Features: Use appropriate commands to enable and configure each security feature (e.g.,
ip ssh version 2,access-list,spanning-tree mode pvst). - Save Configuration: Save your configuration changes to ensure they persist after a reboot.
Remember to consult Packet Tracer's help documentation or the documentation for the specific switch model you're using for the exact commands and syntax.
Best Practices for Switch Security in Packet Tracer Simulations
Beyond the specific features, several best practices should be followed:
- Regularly update your Packet Tracer software: Updates often include security patches and bug fixes that enhance the security of your simulated network.
- Use realistic network topologies: Creating realistic network topologies helps you understand how security features work in real-world scenarios.
- Simulate different attack scenarios: Test your security configurations by attempting different attacks in Packet Tracer to identify potential weaknesses.
- Document your configurations: Keep detailed records of your switch configurations for troubleshooting and future reference.
Conclusion
Securing your network switches is a critical aspect of overall network security. Packet Tracer provides an excellent platform for learning and practicing switch security configurations, mirroring real-world scenarios. By implementing the security features and best practices discussed above, you can significantly enhance your network's security posture and protect against various threats. Remember to continuously learn and update your knowledge to stay ahead of evolving security challenges. Through practical application in environments like Packet Tracer, you'll build a solid foundation in securing your networks against increasingly sophisticated attacks. The consistent use of strong passwords, robust authentication mechanisms, and regular security audits remains critical for maintaining a secure network environment. The use of Packet Tracer simulations provides a safe space for hands-on training, building competency in network security management and response before encountering real-world situations.
Latest Posts
Latest Posts
-
The Martian Chronicles The Martian Summary
Mar 18, 2025
-
Examples Of Questions That Focus On Process Include
Mar 18, 2025
-
Which Statement Is True About First Aid Measures And Hazardous Chemicals
Mar 18, 2025
-
Nurse Toni Is Reviewing The Handout About Iv Pain
Mar 18, 2025
-
Procedure 1 Tracing Blood Flow Patterns
Mar 18, 2025
Related Post
Thank you for visiting our website which covers about 11.6.1 Packet Tracer - Switch Security Configuration . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
