14.1.5 Lab: Configure An Iscsi Target
Onlines
Mar 04, 2025 · 6 min read
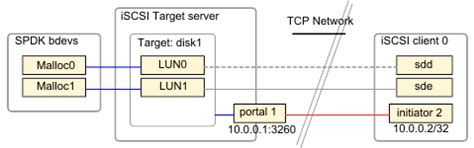
Table of Contents
14.1.5 Lab: Configure an iSCSI Target: A Comprehensive Guide
This comprehensive guide delves into the intricacies of configuring an iSCSI target, walking you through the process step-by-step. We'll explore the essential concepts, configurations, and troubleshooting techniques, ensuring you gain a firm understanding of this crucial storage networking technology. This guide is designed to be highly detailed and practical, mirroring the experience of a hands-on lab environment like the one described in the title.
Understanding iSCSI and its Components
Before diving into the configuration process, let's establish a solid understanding of iSCSI (Internet Small Computer System Interface). iSCSI is a networking protocol that allows data storage facilities, such as hard disk drives, to be accessed remotely over a network using the standard TCP/IP protocol. This essentially means you can access storage devices as if they were locally connected, eliminating the need for direct physical connections.
Key Components of an iSCSI Environment:
- iSCSI Initiator: This is the client that initiates the connection to the storage device. It resides on the computer or server wanting to access the storage. Think of it as the "requester."
- iSCSI Target: This is the storage device that is being accessed remotely. It's the "provider" of the storage. This could be a dedicated storage array, a server with storage attached, or even a virtual machine acting as a storage server.
- iSCSI Target Portal: This is the IP address and port number that the initiator uses to connect to the target. It's the "address" of the storage.
- iSCSI LUN (Logical Unit Number): This is a logical partition on the iSCSI target that represents a separate storage volume. It's like a separate hard drive presented to the initiator.
- CHAP (Challenge-Handshake Authentication Protocol): A security protocol that authenticates the initiator before granting access to the iSCSI target.
Setting Up the iSCSI Target: A Step-by-Step Guide
The specific steps for configuring an iSCSI target depend on the operating system and storage solution you are using. However, the general principles remain consistent. We'll outline a general process, highlighting potential variations and key considerations.
1. Prepare the Storage:
This is the foundational step. You need to identify the storage that will be presented as the iSCSI target. This could be a physical hard drive, a logical volume (like an LVM partition), or a dedicated storage pool. Ensure sufficient space is allocated and formatted appropriately (e.g., ext4, NTFS, XFS depending on your OS).
2. Install and Configure the iSCSI Target Software:
Different operating systems employ different software packages for iSCSI target services. Common options include:
- Linux (e.g., CentOS, Ubuntu):
tgt,openscsiare popular choices. - Windows Server: The built-in iSCSI Target Server feature is readily available.
The installation process varies depending on your chosen OS and package manager. Consult your OS's documentation for specific instructions.
3. Create the iSCSI Target:
After installing the necessary software, you'll need to create the iSCSI target itself. This involves specifying the storage you wish to present, as well as other critical parameters.
Example using tgt on Linux:
The tgt configuration is often handled through configuration files. You'll define the target name, LUNs, and other parameters within these files. This requires a deep understanding of the tgt configuration syntax. Incorrect configuration can lead to issues, so careful attention to detail is essential.
Example using Windows Server's iSCSI Target Server:
The Windows Server interface provides a GUI for creating iSCSI targets. This is generally more user-friendly than the command-line approach used on Linux. You can directly select the disks and create targets via the server manager's interface.
4. Configure CHAP Authentication (Highly Recommended):
For security, implementing CHAP authentication is crucial. This prevents unauthorized access to your iSCSI target. Both the initiator and target need to be configured with matching usernames and passwords. Failure to set up CHAP leaves your storage vulnerable.
5. Configure the iSCSI Target Portal:
The iSCSI target portal defines how initiators connect to the target. You'll need to specify the IP address and port number (typically TCP port 3260). This information will be used by the initiator to establish a connection.
6. Verify the Configuration:
Before allowing initiators to connect, rigorously test your configuration. Tools like iscsiadm on Linux can help verify connectivity and target status. Windows Server's interface also provides tools to check the target's health and status.
Configuring the iSCSI Initiator
Once the iSCSI target is configured, you need to set up the iSCSI initiator on the client machine that will access the storage. Again, the process differs slightly depending on the operating system.
1. Install iSCSI Initiator Software:
Similar to the target, you'll need to install iSCSI initiator software on the client machine. Common options include:
- Linux:
open-iscsiis a widely used initiator. - Windows: The built-in iSCSI Initiator is readily available.
2. Discover the iSCSI Target:
The initiator needs to discover the iSCSI target. This typically involves providing the IP address and port of the iSCSI target portal. The initiator will scan the network and locate the target.
3. Connect to the iSCSI Target:
After discovering the target, the initiator needs to connect to it. This involves specifying the target name and potentially authentication credentials (username and password if CHAP is enabled).
4. Map the iSCSI LUN:
After connecting, the initiator needs to map the iSCSI LUN to a local drive letter (Windows) or device name (Linux). This makes the storage accessible to the operating system.
5. Verify Connectivity and Access:
Once mapped, verify that you can access the storage. Try creating files and directories on the mapped drive to confirm functionality.
Troubleshooting Common iSCSI Issues
Even with careful configuration, you might encounter problems. Here are some common issues and troubleshooting tips:
- Connection Failures: Verify network connectivity, IP addresses, and port numbers. Ensure firewalls are not blocking iSCSI traffic. Check CHAP authentication credentials.
- Authentication Errors: Double-check that the CHAP usernames and passwords on the initiator and target match precisely.
- Access Denied: Ensure the initiator has the necessary permissions to access the iSCSI LUN.
- Performance Issues: Network latency, bandwidth limitations, and storage device performance can affect iSCSI speeds. Analyze network traffic and storage performance metrics.
- Target Not Discovered: Verify the iSCSI target portal is correctly configured and accessible from the initiator's network.
Advanced iSCSI Concepts
This section touches upon more advanced aspects of iSCSI configuration and management.
- Multipathing: This technique allows for multiple network paths to the iSCSI target, improving fault tolerance and performance.
- iSCSI over Fibre Channel (FC-iSCSI): This utilizes Fibre Channel technology as the underlying network transport for iSCSI, potentially offering better performance and reliability.
- Thin Provisioning: This allows for the creation of virtual disks that only consume physical storage as data is written, improving storage efficiency.
- Data Replication: Techniques for replicating iSCSI data to secondary locations for disaster recovery.
Conclusion
Configuring an iSCSI target is a powerful way to share storage across a network. While the process has several steps and requires attention to detail, the benefits of centralized storage management and increased accessibility outweigh the initial complexity. By understanding the components, configuration steps, and troubleshooting techniques, you can successfully implement and maintain a robust iSCSI environment. Remember that thorough planning, careful execution, and regular testing are key to a successful iSCSI deployment. This guide provides a strong foundation; further research into specific operating systems and storage solutions will enhance your expertise in this critical area of storage networking.
Latest Posts
Latest Posts
-
Unit 5 Progress Check Mcq Ap Lang
Mar 05, 2025
-
The First Rule Of Punishment Is
Mar 05, 2025
-
Pride And Prejudice Summary By Chapter
Mar 05, 2025
-
Was Another Common Label For Chicanos Which Means Rotten Fruit
Mar 05, 2025
-
When Surface Preservation Of The Ship Is Required
Mar 05, 2025
Related Post
Thank you for visiting our website which covers about 14.1.5 Lab: Configure An Iscsi Target . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
