A Coworker Tells You To Extract A File
Onlines
Mar 12, 2025 · 5 min read
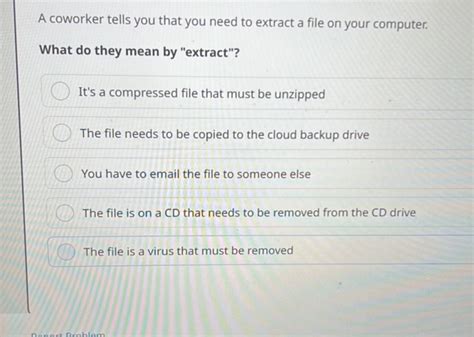
Table of Contents
A Coworker Tells You to Extract a File: Navigating the Risks and Responsibilities
In the interconnected world of modern workplaces, receiving instructions from a coworker to extract a file is a commonplace occurrence. However, this seemingly simple task can harbor significant risks if not approached with caution and awareness. This comprehensive guide explores the various scenarios surrounding this request, emphasizing the importance of security, ethical considerations, and best practices to ensure a safe and productive workflow.
Understanding the Context: Why Extract a File?
Before diving into the security implications, let's examine the common reasons behind a coworker's request to extract a file:
1. Accessing Project Files:
This is the most common scenario. A coworker might need access to specific files within a compressed archive (.zip, .rar, .7z, etc.) for collaboration on a project. This could involve images, documents, code, or other project-related materials.
2. Software Installation or Updates:
Many software programs are distributed as compressed archives. A coworker might ask you to extract a file containing installation files or software updates.
3. Data Transfer and Sharing:
Compressed files are often used to reduce file sizes for easier sharing via email or cloud storage. Extraction becomes necessary to access the individual files after receiving them.
4. Accessing Backup Files:
If data recovery is necessary, compressed backup files might need to be extracted.
Assessing the Risks: Potential Threats and Dangers
While seemingly harmless, extracting a file from an unknown or untrusted source presents several potential risks:
1. Malware Infections:
This is perhaps the most significant threat. Malicious actors can embed malware within seemingly harmless compressed files. Extracting the file can trigger the execution of the malware, potentially leading to:
- Data breaches: Malware can steal sensitive data from your computer.
- System compromise: Malware can take control of your system, potentially allowing remote access to attackers.
- Ransomware attacks: Ransomware can encrypt your files, demanding payment for their release.
- Identity theft: Malware can steal your personal information, putting your identity at risk.
2. Phishing and Social Engineering:
The request itself could be part of a phishing or social engineering attack. A malicious actor might impersonate a coworker, requesting you to extract a file containing malware.
3. Data Leaks:
Even if the file itself is not malicious, extracting it in an unsecured environment or onto an unmanaged device could lead to accidental data leaks.
4. Virus Introduction:
Even if the file is not directly malicious, it could contain viruses or other harmful code that can infect your system upon extraction.
Implementing Security Best Practices: Protecting Yourself and Your Data
To mitigate the risks associated with extracting files from coworkers, follow these crucial steps:
1. Verify the Source:
Before extracting any file, verify the source and legitimacy of the request.
- Confirm the identity of the sender: If you're unsure, contact the coworker directly through a known and trusted communication channel (e.g., internal messaging system) to confirm the request.
- Check email headers and sender details: Look for inconsistencies or suspicious details in emails.
- Question unusual requests: Be wary of requests that seem out of the ordinary or deviate from typical workplace procedures.
2. Scan Files Before Extraction:
Use a reputable antivirus program to scan the compressed file before extracting it. Many antivirus programs offer real-time scanning, which can detect and block threats automatically.
3. Extract Files in a Controlled Environment:
Create a virtual machine (VM) or use a sandboxed environment to extract the file. This isolates the file from your main system, preventing potential damage even if the file contains malware.
4. Review File Extensions and Names:
Examine the file extensions and names carefully. Be cautious of unusual or unexpected file types.
5. Use Caution with Unknown File Types:
Avoid extracting files with unknown or uncommon extensions.
6. Update Your Antivirus Software:
Ensure your antivirus software is up to date with the latest virus definitions.
7. Enable Automatic Updates:
Enable automatic updates for your operating system and software to ensure you have the latest security patches.
Ethical Considerations: Responsibility and Professionalism
Beyond the technical aspects, extracting files from coworkers involves ethical considerations:
1. Respecting Privacy and Confidentiality:
Ensure you have the necessary authorization to access and extract the file. Respect the confidentiality of the data contained within the file.
2. Following Company Policy:
Familiarize yourself with your company's policies regarding file sharing, data security, and acceptable use of company resources. Adhere to these policies rigorously.
3. Reporting Suspicious Activity:
If you encounter a suspicious request or suspect malicious activity, report it to your IT department or security team immediately.
4. Professional Communication:
Maintain clear and professional communication with your coworker regarding the file extraction process. Clarify any uncertainties and document the process.
Best Practices for File Sharing: Avoiding Future Risks
To minimize the need for potentially risky file extraction, consider these best practices:
1. Utilize Secure File Sharing Platforms:
Use your company's approved file-sharing platform or cloud storage service. These platforms often offer security features such as encryption and access controls.
2. Employ Version Control Systems:
For collaborative projects, utilize version control systems (e.g., Git) to manage and track changes to files. This eliminates the need to constantly share large compressed files.
3. Use Encryption for Sensitive Files:
Encrypt sensitive files before sharing them to protect them even if they are intercepted.
4. Implement Strong Passwords:
Use strong and unique passwords for your accounts and devices.
5. Regular Security Audits:
Conduct regular security audits to identify and address vulnerabilities in your systems and processes.
Conclusion: A Proactive Approach to File Extraction
Extracting a file from a coworker, while a seemingly trivial task, can pose significant security and ethical risks. By implementing the security best practices and ethical considerations outlined in this guide, you can significantly reduce your vulnerability to malware, phishing attacks, and data breaches. A proactive and informed approach to file extraction ensures a safe and productive work environment for everyone. Remember, prevention is always better than cure. By fostering a culture of security awareness and responsible file handling, you contribute to a safer digital workspace for yourself and your colleagues. Regularly reviewing and updating your understanding of these security protocols is crucial to maintaining a secure digital presence in the ever-evolving landscape of workplace technology.
Latest Posts
Latest Posts
-
All Of The Following Are Specifics Of Unscheduled Telework Except
Mar 12, 2025
-
You Witch The Original Symbol Of Female Power Answer Key
Mar 12, 2025
-
Stakeholder Blank Is In Direct Contrast With Zero Sum Thinking
Mar 12, 2025
-
De Que Color Es El Tutu De Alicia Alonso
Mar 12, 2025
-
Thompson Simone Biles And The Most Human Meaning Of Courage
Mar 12, 2025
Related Post
Thank you for visiting our website which covers about A Coworker Tells You To Extract A File . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
