Advanced Hardware Lab 7-5: Identify Network Technologies
Onlines
Apr 01, 2025 · 6 min read
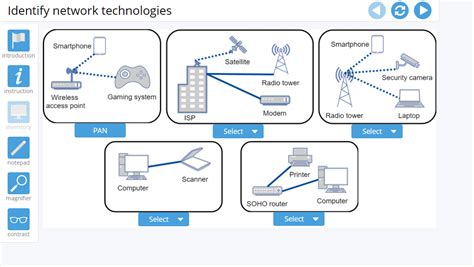
Table of Contents
Advanced Hardware Lab 7-5: Identify Network Technologies
This comprehensive guide delves into the intricacies of Lab 7-5, focusing on identifying various network technologies. We'll move beyond basic identification and explore the underlying principles, practical applications, and troubleshooting techniques for a deeper understanding. This lab is crucial for anyone pursuing a career in networking, systems administration, or cybersecurity. We’ll cover key concepts, practical exercises, and potential troubleshooting scenarios. Let's dive in!
Understanding Network Topologies: The Foundation of Network Identification
Before identifying specific technologies, it’s vital to grasp network topologies. These define how devices connect and communicate within a network. Common topologies include:
1. Bus Topology:
- Description: All devices connect to a single cable (the bus). Simple but suffers from single point of failure.
- Identification: Look for a single cable connecting all devices. A failure on this cable disrupts the entire network.
- Practical Application: Less common in modern networks, historically used in older Ethernet systems.
2. Star Topology:
- Description: All devices connect to a central hub or switch. The most prevalent topology today.
- Identification: Observe a central device (hub or switch) with multiple cables radiating outward to individual devices. Failure of a single cable impacts only one device.
- Practical Application: Found in most homes, offices, and large enterprise networks. Offers scalability and ease of management.
3. Ring Topology:
- Description: Devices connect in a closed loop. Data travels in one direction.
- Identification: Devices are connected in a circular fashion. A break in the ring can disrupt the entire network.
- Practical Application: Less common now, replaced by more robust and scalable alternatives. Used in some specialized applications.
4. Mesh Topology:
- Description: Multiple redundant paths connect devices. Highly reliable and fault-tolerant.
- Identification: Many interconnections between devices providing multiple paths for data transmission. Failure of one connection doesn't necessarily disrupt the network.
- Practical Application: Used in critical infrastructure networks where reliability is paramount, such as military and telecommunications networks.
5. Tree Topology:
- Description: A hierarchical structure, combining aspects of star and bus topologies.
- Identification: Looks like an inverted tree, with a central root node branching out to other nodes.
- Practical Application: Common in larger networks to segment and organize various parts.
Identifying Network Devices: The Hardware Component
Identifying network devices is crucial for understanding the network's architecture and functionality. These key components contribute to a network's overall performance:
1. Network Interface Card (NIC):
- Description: Allows a device (computer, server, etc.) to connect to a network.
- Identification: A physical card inside a computer or a built-in component on a device. Often has an RJ-45 connector for Ethernet cables. Wireless NICs connect via Wi-Fi.
- Troubleshooting: Check for proper driver installation, cable connections, and link lights.
2. Hub:
- Description: A central connection point that broadcasts data to all connected devices. Simpler than switches.
- Identification: A box with multiple ports for connecting cables. All connected devices receive all data transmissions (collision domain).
- Troubleshooting: Check cable connections, power supply, and replace if faulty. Generally less common in modern networks.
3. Switch:
- Description: A more intelligent device that forwards data only to the intended recipient, improving network efficiency.
- Identification: Similar to a hub but with more advanced features and management capabilities. Often has LED indicators for link status and port activity.
- Troubleshooting: Check for proper configuration, port status, and link lights. Consider replacing if there are persistent connectivity issues.
4. Router:
- Description: Connects different networks, typically using different IP addresses. Directs traffic between networks.
- Identification: Has multiple ports for connecting to different networks, and often features configuration interfaces.
- Troubleshooting: Check IP address configuration, routing tables, and connectivity to other networks. Restarting the router can often resolve simple issues.
5. Modem:
- Description: Modulates and demodulates signals, converting digital data to analog signals (and vice versa) for transmission over a physical medium like phone lines or cable.
- Identification: Connects to a broadband internet service provider (ISP) and typically has lights indicating connection status and activity.
- Troubleshooting: Check connection to the ISP, power supply, and signal strength.
Network Protocols: The Language of Networking
Network protocols govern how data is transmitted across a network. Understanding these protocols is essential for effective network identification and troubleshooting:
1. TCP/IP (Transmission Control Protocol/Internet Protocol):
- Description: The foundation of the internet, providing reliable and unreliable data transmission. TCP provides connection-oriented, reliable data transfer, while IP handles addressing and routing.
- Identification: The dominant protocol on the internet. Look for IP addresses (e.g., 192.168.1.100) and TCP port numbers (e.g., port 80 for HTTP).
- Troubleshooting: Check IP address configuration, DNS settings, and firewall rules. Ping commands can verify network connectivity.
2. HTTP (Hypertext Transfer Protocol):
- Description: Used for communication between web browsers and web servers.
- Identification: Port 80 (HTTP) or 443 (HTTPS). Used for browsing websites.
- Troubleshooting: Check web server configuration, browser settings, and network connectivity.
3. FTP (File Transfer Protocol):
- Description: Used for transferring files between computers.
- Identification: Port 20 and 21. Look for file transfer activity.
- Troubleshooting: Check file permissions, server availability, and network connectivity.
4. SMTP (Simple Mail Transfer Protocol):
- Description: Used for sending emails.
- Identification: Port 25. Observe email traffic.
- Troubleshooting: Check email server configuration, DNS settings, and firewall rules.
5. DNS (Domain Name System):
- Description: Translates domain names (e.g., google.com) into IP addresses.
- Identification: Used by all applications requiring network addresses. Look for DNS server addresses in network settings.
- Troubleshooting: Check DNS server settings, DNS resolution, and network connectivity.
Practical Exercises and Advanced Considerations
This section explores practical exercises and advanced concepts related to identifying network technologies:
Exercise 1: Network Topology Identification
Given a diagram or physical network setup, identify the topology (bus, star, ring, mesh, tree). Analyze the connections between devices to determine the overall network structure.
Exercise 2: Device Identification
Examine a network and identify different devices such as hubs, switches, routers, and modems. Observe their physical characteristics and functions.
Exercise 3: Protocol Identification
Use network monitoring tools (like Wireshark – remember to use this responsibly and ethically, and only on networks you have permission to monitor) to capture network traffic and identify the protocols being used (TCP/IP, HTTP, FTP, etc.). Analyze the packet headers to determine the protocols and ports involved.
Advanced Concepts:
- VLANs (Virtual LANs): Logical separation of a network into smaller, isolated broadcast domains. These improve security and performance.
- Subnetting: Dividing a network into smaller subnetworks for better management and efficiency.
- Network Security: Implementing firewalls, intrusion detection systems, and other security measures to protect the network from unauthorized access.
Troubleshooting Common Network Issues
This section provides guidance for troubleshooting common network problems:
- Connectivity Issues: Check cable connections, device power, and network configuration. Try restarting devices.
- Slow Network Speed: Investigate network congestion, bandwidth limitations, and potential bottlenecks.
- Network Outages: Check for power failures, cable damage, and router/switch malfunctions. Contact the ISP if the problem originates outside the local network.
- Security Breaches: Monitor network traffic for suspicious activity. Implement strong passwords and security measures.
Conclusion
Mastering the identification of network technologies is vital for any aspiring network professional. This lab provides a solid foundation for understanding various topologies, devices, protocols, and troubleshooting techniques. By building upon this knowledge, you can effectively manage, troubleshoot, and secure networks of any size and complexity. Remember to continue exploring advanced concepts and expanding your skillset to stay ahead in the ever-evolving world of networking. Continuous learning and practical experience are key to success in this dynamic field. Further research into specific network technologies and security protocols will significantly enhance your understanding and ability to address real-world challenges.
Latest Posts
Latest Posts
-
Time Phased Activation Might Be Appropriate For
Apr 02, 2025
-
Match A Supplement Compound To The Ergogenic Functional Claim
Apr 02, 2025
-
Unidad 5 Leccion 2 Answer Key
Apr 02, 2025
-
Romeo And Juliet Character Map Answers
Apr 02, 2025
-
Which Type Of Shock Occurs From An Antigen Antibody Response
Apr 02, 2025
Related Post
Thank you for visiting our website which covers about Advanced Hardware Lab 7-5: Identify Network Technologies . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
