During The Aaa Process When Will Authorization Be Implemented
Onlines
Apr 06, 2025 · 6 min read
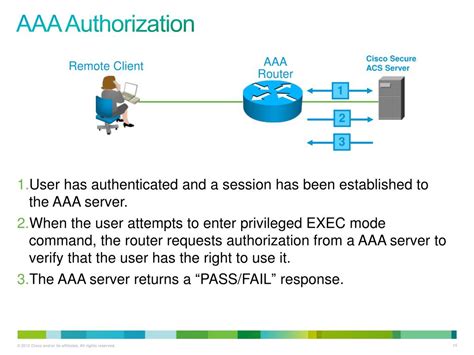
Table of Contents
When Will Authorization Be Implemented During the AAA Process?
The AAA process – Authentication, Authorization, and Accounting – is a critical security framework for controlling access to network resources. While authentication verifies the user's identity, authorization determines what that user is permitted to do. This article delves into the timing of authorization within the AAA process, exploring different scenarios and technologies. Understanding this crucial step is paramount for establishing robust and secure network environments.
Understanding the AAA Process Flow
Before diving into the authorization implementation timing, it's crucial to understand the overall flow of the AAA process. The process typically unfolds in the following order:
-
Authentication: The user initiates a request to access a resource. The system first verifies the user's identity, usually through a username and password, certificate, or multi-factor authentication (MFA). This stage confirms who the user is.
-
Authorization: Once authenticated, the system determines what actions the user is permitted to perform. This involves checking access control lists (ACLs), roles, and policies to establish what the user can do. This stage is the focus of this article.
-
Accounting: After the user accesses the resource, the system logs details of the interaction, such as duration, resources accessed, and actions performed. This stage tracks what the user did.
When Does Authorization Occur?
The timing of authorization within the AAA process isn't a single fixed point. Instead, it's highly dependent on the specific implementation and the type of access being requested. Here are some key scenarios:
1. Authorization Before Access (Most Common):
This is the most prevalent and secure approach. Authorization happens before the user gains access to the requested resource. The authentication process triggers the authorization check. If the user lacks the necessary permissions, access is denied immediately. This prevents unauthorized access altogether.
-
Example: A user attempts to log into a company's internal network. After successful authentication, the system immediately checks the user's access rights to the network. If the user only has access to specific departments or applications, access is granted accordingly; otherwise, access is denied.
-
Advantages: Highest security, prevents unauthorized access, simplifies auditing.
-
Disadvantages: Can add latency if authorization checks are complex or slow.
2. Authorization After Initial Access (Less Common, Higher Risk):
In some cases, authorization might occur after the user has gained initial access. This usually involves a system where a more comprehensive authorization check is performed once inside a protected area, but access is granted initially upon successful authentication. This approach is generally less secure and should only be employed with careful consideration of the risks involved.
-
Example: A user authenticates to a web application portal. They gain access to a dashboard, and then further authorization is performed based on the specific features or sections they attempt to access within the dashboard.
-
Advantages: Allows for more granular access control within a protected environment, can streamline initial access.
-
Disadvantages: Higher risk of unauthorized access during the initial period before authorization, requires more robust internal security mechanisms.
3. Dynamic Authorization (Increasingly Common):
With the rise of cloud computing and microservices, dynamic authorization is becoming increasingly prevalent. This approach allows authorization decisions to change based on several factors such as time of day, user location, and even the current state of the system. The authorization check isn't a single event but a continuous process.
-
Example: A user attempts to access a specific cloud-based application. The system checks the user's role, location, time of day, and the current system load to determine if access should be granted. This allows for adaptive security and resource management.
-
Advantages: Enhanced security, adaptive access control, optimized resource utilization.
-
Disadvantages: Increased complexity in implementation and management, requires advanced technologies and skilled personnel.
4. Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC):
These are two common authorization models impacting implementation timing. RBAC assigns permissions based on user roles, while ABAC uses attributes of users, resources, and environments to determine access. Both significantly influence when and how authorization occurs.
-
RBAC: Authorization is often pre-determined and relatively quick since the roles and permissions are already defined.
-
ABAC: Authorization can involve more complex calculations and evaluations depending on the attribute combination, potentially adding to processing time.
Technologies Influencing Authorization Implementation
Various technologies play a significant role in the timing and implementation of authorization within the AAA process:
-
RADIUS (Remote Authentication Dial-In User Service): A widely used networking protocol that provides centralized authentication, authorization, and accounting management. Authorization typically occurs before access is granted.
-
TACACS+ (Terminal Access Controller Access-Control System Plus): Another widely used protocol, similar to RADIUS, but offering enhanced security features and more granular control over authorization. Authorization usually takes place before access is granted.
-
LDAP (Lightweight Directory Access Protocol): A directory service protocol for accessing and managing directory information. It's often integrated with AAA systems for storing user information and authorization policies. Authorization depends on the specific implementation but usually happens before access.
-
OAuth 2.0 and OpenID Connect: These protocols are commonly used for authorization in web applications and APIs. Authorization typically occurs through token exchange, and access is granted or denied based on the token's validity and scopes. This often happens before access is granted.
-
Cloud-based Identity and Access Management (IAM) Systems: These systems provide centralized management of user identities and access permissions, often employing dynamic authorization techniques. The timing depends on the specific system architecture and configuration.
Optimizing Authorization for Performance and Security
Efficient authorization implementation is crucial for both security and performance. Poorly implemented authorization can lead to slow response times, security vulnerabilities, and poor user experience. Here are some key optimization strategies:
-
Caching: Caching authorization decisions can significantly reduce latency, especially for frequently accessed resources.
-
Efficient Data Structures: Employing efficient data structures like B-trees or hash tables can improve the speed of authorization checks.
-
Policy Optimization: Regularly review and optimize access control policies to ensure they're both secure and efficient.
-
Load Balancing: Distributing authorization requests across multiple servers can prevent bottlenecks.
-
Regular Auditing: Monitor authorization logs to detect and address any security breaches or policy violations.
Conclusion
The timing of authorization within the AAA process is a critical aspect of network security. While the most common and secure method involves authorization before access, other scenarios exist. The specific implementation heavily depends on factors such as the chosen technologies, access control models (RBAC, ABAC), and the complexity of the authorization policies. Understanding this nuance is essential for establishing robust, secure, and efficient access control mechanisms in any network environment. By employing optimal strategies and technologies, organizations can strike a balance between security and performance, ensuring a smooth and secure user experience. The ongoing evolution of authorization technologies will continue to refine the implementation and timing of this crucial security step.
Latest Posts
Latest Posts
-
Complete The Following Statement Universal Education Does Not Involve
Apr 07, 2025
-
Hair Analysis Can Reveal All But Which Of The Following
Apr 07, 2025
-
The Spot Where You Can No Longer Stop Safely Is
Apr 07, 2025
-
Summary Of To Kill A Mockingbird Chapter 2
Apr 07, 2025
-
Which Of The Following Statements Is True About Apcs
Apr 07, 2025
Related Post
Thank you for visiting our website which covers about During The Aaa Process When Will Authorization Be Implemented . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
