Lab 8-4 Testing Mode Identify Tcp-ip Protocols And Port Numbers
Onlines
Mar 22, 2025 · 7 min read
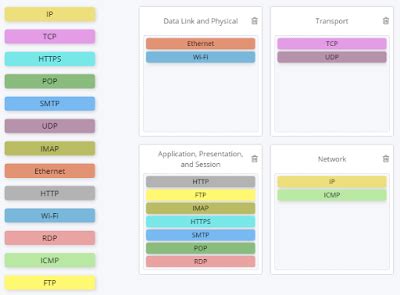
Table of Contents
Lab 8-4: Testing Mode – Identifying TCP/IP Protocols and Port Numbers: A Deep Dive
This comprehensive guide delves into the intricacies of Lab 8-4, focusing on identifying TCP/IP protocols and their associated port numbers in a testing environment. We'll explore various methods for identifying these crucial components of network communication, emphasizing practical application and troubleshooting techniques. Understanding TCP/IP protocols and ports is fundamental to network administration, security, and troubleshooting, making this lab a cornerstone of networking education.
Understanding the Basics: TCP/IP Protocols and Ports
Before diving into the lab specifics, let's solidify our understanding of the core concepts:
TCP/IP: The Foundation of the Internet
The Transmission Control Protocol/Internet Protocol (TCP/IP) suite is the foundation of the internet and most modern computer networks. It defines how data is transmitted across networks, ensuring reliable and efficient communication between devices. This suite is comprised of numerous protocols, each with specific functions:
- IP (Internet Protocol): Responsible for addressing and routing packets across networks. It's connectionless, meaning it doesn't guarantee delivery.
- TCP (Transmission Control Protocol): Provides a reliable, connection-oriented service on top of IP. It guarantees delivery, ordering, and error checking of data.
- UDP (User Datagram Protocol): Another protocol built on top of IP, but unlike TCP, it's connectionless and doesn't guarantee delivery. It prioritizes speed over reliability. It's often used for applications where a small delay is acceptable over guaranteed delivery.
These are just a few of the numerous protocols within the TCP/IP suite. Others include ICMP (Internet Control Message Protocol) used for network diagnostics (like ping), and HTTP (Hypertext Transfer Protocol) used for web browsing.
Port Numbers: The Address within an Address
While IP addresses identify a device on a network, port numbers identify specific applications or services running on that device. Think of it like the address on a building – the IP address is the street address, while the port number is the specific apartment or office number.
Port numbers range from 0 to 65535. These are divided into:
- Well-known ports (0-1023): These are reserved for standard services, like HTTP (port 80), HTTPS (port 443), FTP (ports 20 and 21), and SMTP (port 25). These are usually assigned by the Internet Assigned Numbers Authority (IANA).
- Registered ports (1024-49151): These are assigned by IANA to specific applications, but can be reused for other applications if not officially assigned.
- Dynamic or private ports (49152-65535): These ports are typically used for temporary connections and are automatically assigned by the operating system.
Knowing these port numbers is essential for network administration and security. For instance, blocking port 22 (SSH) prevents unauthorized remote access to a server.
Lab 8-4: Practical Application and Methodology
Now, let's tackle the specifics of Lab 8-4, which focuses on identifying TCP/IP protocols and port numbers using various testing methods. The precise methods will vary based on your specific lab environment (physical or virtual), but the underlying principles remain consistent.
Method 1: Using netstat (or ss on newer Linux systems)
The netstat command (or ss, its successor) is a powerful command-line utility that provides detailed information about network connections, routing tables, interface statistics, and more. It's an invaluable tool for identifying active TCP/IP connections and their associated protocols and port numbers.
Example (Linux):
sudo netstat -anp # Shows all active connections, listening ports, and the process associated with them
Explanation:
-a: Shows all connections and listening ports.-n: Displays numerical addresses and port numbers instead of resolving hostnames.-p: Shows the process ID and name associated with each connection.
Interpreting the Output:
The output will display a list of connections, including the local IP address and port, the foreign IP address and port, the state of the connection (e.g., ESTABLISHED, LISTEN, CLOSE_WAIT), and the process ID and name. By examining the port number, you can determine the protocol being used. For example, a connection using port 80 indicates HTTP traffic.
Method 2: Using tcpdump or Wireshark (Packet Capture and Analysis)
For a more in-depth analysis, packet capture tools like tcpdump (command-line) or Wireshark (GUI) are extremely useful. These tools allow you to capture and analyze network traffic, enabling you to identify protocols and ports within individual packets.
Example (Linux, tcpdump):
sudo tcpdump -i eth0 port 80 # Captures packets on interface eth0 with port 80 (HTTP)
Explanation:
-i eth0: Specifies the network interface to capture traffic from. Replaceeth0with your interface name.port 80: Filters the captured packets to only include those using port 80.
Interpreting the Output:
The output shows a detailed breakdown of each captured packet, including the source and destination IP addresses and ports, the protocol, and the packet data. This provides a much more detailed view of network communications than netstat. Wireshark provides a visual and user-friendly interface for analyzing this captured data.
Method 3: Examining System Logs
System logs often contain valuable information about network activity, including information about TCP/IP protocols and ports used by different services. The exact location of these logs varies depending on the operating system and service. However, common log locations include:
- /var/log/syslog (Linux)
- /var/log/messages (Linux)
- Event Viewer (Windows)
Examining these logs can help identify any issues related to specific protocols or ports, especially if you are troubleshooting a network problem.
Method 4: Using Port Scanning Tools (Ethical Considerations)
While port scanning tools like Nmap can be useful for identifying open ports on a system, it’s crucial to use them ethically and only on systems you have permission to scan. Unauthorized port scanning is illegal and can lead to serious consequences. If you are conducting this lab, you are almost certainly already in a controlled environment where this is permitted.
Example (using Nmap - requires administrator/root privileges):
sudo nmap -sT
Explanation:
-sT: Performs a TCP connect scan. Other scan types are available with different options.<target_ip_address>: Replace this with the IP address of the target system.
Interpreting the Output:
Nmap provides a detailed report of the open ports on the target system, along with information about the services associated with those ports.
Troubleshooting Common Issues
During Lab 8-4, you might encounter several challenges. Here are some common issues and their solutions:
- Permission Errors: If you encounter permission errors when using commands like
netstatortcpdump, you'll likely need to run them withsudo(Linux) or as an administrator (Windows). - Incorrect Interface Name: When using
tcpdump, ensure you specify the correct network interface name. Useip addr(Linux) oripconfig(Windows) to identify the correct name. - Firewall Interference: Firewalls can block network traffic, preventing you from capturing packets or seeing certain connections. Temporarily disabling the firewall (for testing purposes only) can help troubleshoot this issue. Remember to re-enable the firewall afterwards.
- Complex Network Configurations: In complex networks, interpreting the output of
netstatortcpdumpcan be challenging. Focus on understanding the basic principles, and break down the analysis into smaller, manageable parts.
Advanced Concepts and Further Exploration
Once you've mastered the fundamentals of Lab 8-4, you can delve into more advanced topics:
- Firewall Rules: Understand how firewall rules can filter network traffic based on protocols and port numbers.
- Network Security: Learn how identifying open ports is crucial for securing your network against malicious attacks.
- Service Discovery: Explore techniques for automatically discovering services running on a network.
- Network Monitoring: Implement network monitoring tools to track network activity and performance.
Conclusion
Lab 8-4 provides a fundamental introduction to identifying TCP/IP protocols and port numbers, crucial skills for any network administrator or security professional. By mastering the techniques outlined in this guide, you’ll gain a deeper understanding of network communication, enabling you to effectively troubleshoot issues, secure your network, and monitor its performance. Remember to always perform these actions ethically and responsibly, adhering to relevant laws and regulations. Through continued practice and exploration, you'll solidify your expertise in this essential area of networking.
Latest Posts
Latest Posts
-
Elite High School Entebbe Fees Structure
Mar 22, 2025
-
1 14 Infinite Limits And Vertical Asymptotes
Mar 22, 2025
-
You Re Booking Flights For Two Visiting Clients
Mar 22, 2025
-
Apes Unit 8 Progress Check Mcq Part B
Mar 22, 2025
-
Patterns For College Writing 15th Edition Pdf
Mar 22, 2025
Related Post
Thank you for visiting our website which covers about Lab 8-4 Testing Mode Identify Tcp-ip Protocols And Port Numbers . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
