Match The Application Protocols To The Correct Transport Protocols.
Onlines
Apr 02, 2025 · 6 min read
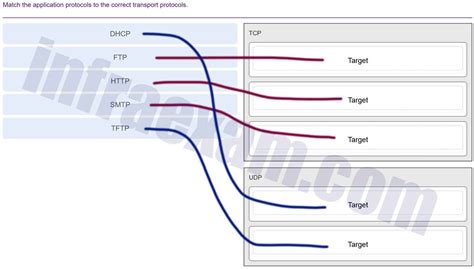
Table of Contents
Matching Application Protocols to Correct Transport Protocols: A Comprehensive Guide
The internet, a vast network connecting billions of devices, relies on a layered architecture to ensure seamless communication. At the heart of this architecture lies the interplay between application protocols and transport protocols. Understanding this relationship is crucial for developers, network administrators, and anyone seeking a deeper understanding of how the internet functions. This comprehensive guide delves into the intricacies of matching application protocols to their appropriate transport protocols, exploring the functionalities, advantages, and disadvantages of each.
Understanding the Layered Architecture
Before diving into specific protocol pairings, it's essential to grasp the fundamental layered model of network communication, typically represented by the TCP/IP model. This model simplifies the complexities of networking into four layers:
-
Application Layer: This is where applications interact directly with the network. Examples include HTTP (web browsing), SMTP (email), FTP (file transfer), and DNS (domain name resolution). Application protocols define the structure and semantics of the data exchanged between applications.
-
Transport Layer: This layer provides reliable or unreliable data transfer services between applications. The two primary transport protocols are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). They handle segmentation, reassembly, flow control, and error detection/correction.
-
Network Layer (Internet Layer): This layer handles routing packets across networks. The primary protocol here is IP (Internet Protocol), which addresses and routes data packets.
-
Link Layer (Data Link Layer): This layer handles physical transmission of data over a specific medium, such as Ethernet or Wi-Fi. Protocols at this layer manage access to the physical medium.
The focus of this article is on the relationship between the application and transport layers. The correct pairing of these protocols ensures efficient and reliable data transfer.
TCP (Transmission Control Protocol): The Reliable Workhorse
TCP is a connection-oriented, reliable transport protocol. This means it establishes a dedicated connection between the sender and receiver before transferring data. Key features of TCP include:
-
Connection-Oriented: A three-way handshake is performed to establish a connection before data transfer. This ensures both ends are ready to communicate.
-
Reliable Data Delivery: TCP uses sequence numbers, acknowledgments (ACKs), and retransmissions to ensure reliable delivery of data. Lost or corrupted packets are detected and retransmitted.
-
Ordered Data Delivery: TCP guarantees that data arrives in the same order it was sent.
-
Flow Control: TCP prevents a fast sender from overwhelming a slow receiver through mechanisms like sliding windows.
-
Congestion Control: TCP algorithms help manage network congestion by adjusting transmission rates based on network conditions.
Because of its reliability and ordered delivery, TCP is well-suited for applications requiring high data integrity and predictable performance.
Application Protocols using TCP:
-
HTTP (Hypertext Transfer Protocol): The foundation of the World Wide Web, HTTP is used for transferring web pages and other resources between web servers and clients. Its reliance on TCP ensures reliable delivery of web content. HTTP/2 and HTTP/3 build upon this foundation with improved performance characteristics.
-
HTTPS (Hypertext Transfer Protocol Secure): The secure version of HTTP, HTTPS utilizes TCP in conjunction with SSL/TLS encryption to protect data transmitted over the internet. This is crucial for securing sensitive information like passwords and credit card details.
-
SMTP (Simple Mail Transfer Protocol): Used for sending emails, SMTP relies on TCP for reliable delivery of email messages. The reliability ensures that emails are not lost or corrupted during transmission.
-
FTP (File Transfer Protocol): FTP uses TCP to transfer files between a client and a server. It provides features for uploading, downloading, and managing files remotely.
-
POP3 (Post Office Protocol version 3): Used for retrieving emails from a mail server, POP3 employs TCP to ensure reliable download of email messages.
-
IMAP (Internet Message Access Protocol): IMAP also handles email retrieval, but unlike POP3, it allows users to manage emails on the server. It also uses TCP for reliable communication.
UDP (User Datagram Protocol): The Speedy Messenger
UDP is a connectionless, unreliable transport protocol. Unlike TCP, it doesn't establish a connection before sending data. This results in faster data transmission but with the trade-off of reliability. Key features of UDP include:
-
Connectionless: No connection setup is required. Data is sent as individual datagrams without establishing a dedicated connection.
-
Unreliable Data Delivery: UDP doesn't guarantee delivery or order of data packets. Lost or corrupted packets are not retransmitted.
-
Lightweight: UDP has a smaller header than TCP, resulting in lower overhead.
-
Low Latency: The lack of connection setup and error checking makes UDP faster than TCP, especially for real-time applications.
UDP is ideal for applications where speed is prioritized over reliability, such as real-time streaming and online gaming. The loss of a few packets is generally acceptable in these scenarios.
Application Protocols using UDP:
-
DNS (Domain Name System): DNS translates domain names (e.g., www.google.com) into IP addresses. While DNS can use TCP for zone transfers, it primarily uses UDP for its query-response mechanism because of the speed requirement for name resolution.
-
DHCP (Dynamic Host Configuration Protocol): DHCP automatically assigns IP addresses to devices on a network. It uses UDP for its fast, broadcast-based communication.
-
SNMP (Simple Network Management Protocol): SNMP is used for monitoring and managing network devices. It often uses UDP for its efficient polling of network devices.
-
RTP (Real-time Transport Protocol): RTP is designed for real-time streaming applications like video conferencing and online gaming. It prioritizes speed over guaranteed delivery, accepting some packet loss.
-
RTCP (RTP Control Protocol): Works in conjunction with RTP to provide feedback on the quality of the real-time stream. It's also UDP based.
-
TFTP (Trivial File Transfer Protocol): A simplified version of FTP, TFTP often uses UDP for its file transfer operations. It's less reliable than FTP but faster.
Choosing the Right Transport Protocol: Key Considerations
The selection of the appropriate transport protocol depends heavily on the requirements of the application:
-
Reliability: If data integrity and guaranteed delivery are paramount (e.g., financial transactions, file transfers), TCP is the preferred choice.
-
Speed: For applications where speed is crucial and some data loss is acceptable (e.g., online gaming, video streaming), UDP is a better option.
-
Latency: UDP's connectionless nature leads to lower latency, making it suitable for real-time applications.
-
Overhead: UDP's smaller header size results in lower overhead, further contributing to its speed advantage.
-
Congestion Control: TCP's sophisticated congestion control mechanisms are essential for preventing network congestion, especially in high-bandwidth scenarios.
Advanced Scenarios and Protocol Combinations
The world of networking is not always black and white. Some applications employ sophisticated strategies, using multiple protocols or dynamically switching between TCP and UDP depending on network conditions. For example:
-
VOIP (Voice over IP) systems: Often utilize both UDP and TCP. UDP is used for real-time voice transmission while TCP might handle signaling and control information.
-
Adaptive protocols: These protocols dynamically adjust their behavior based on network conditions, choosing the optimal transport protocol for different segments of the communication.
-
Multiplexing: A single TCP connection can be used to carry multiple streams of data, improving efficiency and reducing overhead.
Conclusion: Mastering the Protocol Partnership
Understanding the relationship between application protocols and transport protocols is essential for anyone working with network technologies. The choice between TCP and UDP involves a careful balancing act between reliability and speed. By understanding the strengths and weaknesses of each protocol, developers and network administrators can make informed decisions that optimize network performance and ensure the reliable operation of internet applications. As network technology continues to evolve, this knowledge becomes even more critical for managing the complexities of the digital landscape. Remember to always consider the specific needs of your application when making the crucial decision of pairing application and transport protocols for optimal functionality and performance.
Latest Posts
Latest Posts
-
Chapter 2 Pedagogy Of The Oppressed
Apr 03, 2025
-
Which Is Not Recommended When Giving Feedback
Apr 03, 2025
-
A Simple Elevator Ride Can Teach
Apr 03, 2025
-
Penelope 1 Of 1 Muestra Sus Fotos A Mi
Apr 03, 2025
-
What Property Of Oil Makes It Float On Water
Apr 03, 2025
Related Post
Thank you for visiting our website which covers about Match The Application Protocols To The Correct Transport Protocols. . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
