What Is Opsec Select All That Apply
Onlines
Mar 10, 2025 · 7 min read
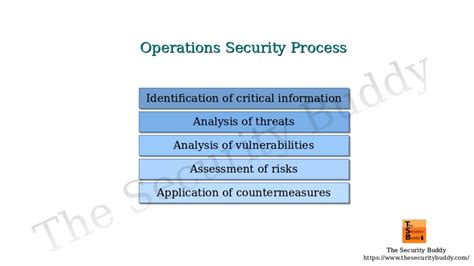
Table of Contents
What is OPSEC? Select All That Apply
Operational Security (OPSEC) is a critical process for protecting sensitive information and maintaining a secure operational environment. It's not just about cybersecurity; it encompasses a broader range of practices designed to mitigate risks across various aspects of an organization or individual's activities. Understanding OPSEC is crucial for safeguarding against threats, protecting valuable assets, and maintaining a competitive edge. This comprehensive guide delves into the multifaceted nature of OPSEC, exploring its key principles, methods, and applications.
Defining OPSEC: More Than Just Cybersecurity
OPSEC is often misunderstood as a synonym for cybersecurity, but it's far more encompassing. While cybersecurity focuses on digital threats, OPSEC encompasses all aspects of security that protect an organization's operations and interests from adversaries. This includes physical security, personnel security, communications security, and more. Think of it as a holistic approach to risk management, aiming to prevent adversaries from gaining actionable intelligence.
Key elements that define OPSEC:
- Identifying Critical Information: This is the foundation of OPSEC. It involves pinpointing the data, processes, or activities that, if compromised, would significantly harm your organization or mission. This isn't just about classified information; it also includes seemingly innocuous details that, when pieced together, could reveal sensitive information.
- Analyzing Threats: Understanding who your adversaries are, their capabilities, and their intentions is essential. This involves assessing potential threats from competitors, nation-states, activists, or even disgruntled employees.
- Analyzing Vulnerabilities: This stage involves identifying weaknesses in your security posture that adversaries could exploit to access critical information. This might include physical vulnerabilities (unsecured buildings), technical vulnerabilities (software bugs), or human vulnerabilities (lack of security awareness training).
- Developing Countermeasures: Based on the threat and vulnerability analysis, you develop specific measures to mitigate the risks. This could involve implementing technical controls (firewalls, intrusion detection systems), physical controls (access control systems, surveillance cameras), and administrative controls (security policies, training programs).
- Implementing and Monitoring: The countermeasures must be implemented effectively and monitored regularly to ensure their ongoing effectiveness. Regular reviews and updates are crucial to adapt to evolving threats.
OPSEC Principles: A Foundation for Success
Effective OPSEC relies on several core principles that guide the process and ensure its effectiveness. Understanding these principles is key to building a robust OPSEC program:
- Need-to-Know Basis: Only individuals who absolutely need access to sensitive information should be granted access. Limiting access reduces the risk of leaks and compromises.
- Minimize Exposure: Keep sensitive information close to the vest. Avoid unnecessary discussions or displays of sensitive materials. Reduce the amount of information available to potential adversaries.
- Compartmentalization: Divide sensitive information into smaller, isolated compartments. If one compartment is compromised, the damage is limited.
- Security Awareness Training: Educate personnel about OPSEC principles and procedures. Training helps employees identify and avoid potential risks.
- Continuous Improvement: OPSEC is an ongoing process, not a one-time fix. Regularly review and update your OPSEC plan to adapt to evolving threats and vulnerabilities.
- Information Security Management Systems (ISMS): Integrate OPSEC into a broader ISMS framework. This ensures a comprehensive and coordinated approach to information security.
OPSEC Methods: Practical Application
OPSEC isn't just a theoretical concept; it involves practical methods and techniques to protect sensitive information. Here are some key methods used in OPSEC:
- Physical Security Measures: This includes securing facilities, controlling access, using surveillance systems, and managing physical assets to prevent unauthorized access or theft.
- Communication Security: This focuses on protecting communications channels from interception or manipulation. This might involve using encryption, secure messaging apps, or implementing strict protocols for handling sensitive information.
- Personnel Security: This includes background checks, security clearances, and training to ensure employees understand their responsibilities in maintaining OPSEC.
- Data Security: This involves protecting sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction. This might involve data encryption, access controls, and data loss prevention (DLP) measures.
- Social Engineering Awareness: Training employees to recognize and avoid social engineering attacks, which often exploit human vulnerabilities to gain access to sensitive information.
- Network Security: Implementing firewalls, intrusion detection systems, and other network security measures to protect against cyberattacks.
OPSEC and Different Sectors: Tailored Approaches
The implementation of OPSEC varies depending on the specific sector and the nature of the organization's activities. Here are some examples:
1. Military: Military OPSEC is critical for protecting operational plans, troop deployments, and sensitive technologies from enemy intelligence. It involves strict protocols for communication, information handling, and physical security.
2. Government: Government agencies handle a vast amount of sensitive information, including national security secrets and citizen data. OPSEC is vital for protecting this information from both foreign and domestic threats.
3. Corporations: Businesses, particularly those in competitive industries or handling sensitive financial information, use OPSEC to protect trade secrets, intellectual property, and customer data from competitors or malicious actors.
4. Non-profit Organizations: Even non-profit organizations can be targets of malicious actors, and OPSEC measures are necessary to protect donor data, confidential internal information, and operational assets.
What is OPSEC? Select All That Apply - Quiz
To test your understanding of OPSEC, consider the following scenarios. Select all the options that represent effective OPSEC practices:
(Select all that apply)
A. Regularly updating software and patching vulnerabilities on all company devices. B. Sharing detailed travel itineraries with colleagues and posting them on social media. C. Implementing strong password policies and multi-factor authentication. D. Leaving sensitive documents unattended on a desk. E. Conducting thorough background checks on employees who handle confidential information. F. Using unencrypted email to send sensitive financial data. G. Regularly reviewing and updating OPSEC policies and procedures. H. Disposing of sensitive documents securely (shredding, incineration).
Answers: A, C, E, G, H
OPSEC in the Digital Age: Addressing New Challenges
The digital age presents new challenges and opportunities for OPSEC. The proliferation of digital technologies, the increasing interconnectedness of systems, and the rise of sophisticated cyber threats require a proactive and adaptable OPSEC approach. Key considerations include:
- Cybersecurity Hygiene: Implementing robust cybersecurity measures, including firewalls, intrusion detection systems, and regular security audits, is critical for protecting digital assets.
- Data Encryption: Encrypting sensitive data both in transit and at rest is crucial for protecting it from unauthorized access.
- Social Media Awareness: Employees need training to understand the risks associated with using social media and how their online activities can compromise OPSEC.
- Mobile Device Security: Protecting mobile devices from theft or hacking is essential, as these devices often contain sensitive information.
- Cloud Security: If using cloud services, ensure they comply with relevant security standards and implement appropriate access controls.
- Supply Chain Security: Protecting your supply chain from vulnerabilities is crucial as compromised suppliers can provide entry points for attackers.
Integrating OPSEC into Your Organization: A Step-by-Step Guide
Implementing a comprehensive OPSEC program requires a structured approach. Here's a step-by-step guide to get you started:
- Conduct a Risk Assessment: Identify your critical assets and potential threats.
- Develop an OPSEC Plan: Document your OPSEC procedures and assign responsibilities.
- Implement Security Controls: Put your OPSEC plan into action.
- Train Your Personnel: Educate your employees about OPSEC principles and procedures.
- Monitor and Review: Regularly assess the effectiveness of your OPSEC program and make adjustments as needed.
- Stay Informed: Keep up-to-date on the latest threats and vulnerabilities.
Conclusion: The Importance of Proactive OPSEC
OPSEC is not a luxury; it's a necessity for any organization that values the protection of its sensitive information and operational integrity. By proactively implementing a robust OPSEC program, organizations can significantly reduce their risk of compromise, protect their valuable assets, and maintain a competitive edge in today's challenging security landscape. Remember, a strong OPSEC program is a continuous process of assessment, adaptation, and improvement. It's an investment in the long-term security and success of your organization. By understanding and implementing the principles and methods outlined in this guide, you can build a strong foundation for protecting your organization's most valuable assets.
Latest Posts
Latest Posts
-
Unit 3 Progress Check Mcq Apush
Mar 10, 2025
-
In The Hands Of An Angry God Summary
Mar 10, 2025
-
Till We Have Faces Summary Chapter 1
Mar 10, 2025
-
Angela And Carlos Are Asked To Determine The Relationship
Mar 10, 2025
-
If Wxyz Is A Square Which Statements Must Be True
Mar 10, 2025
Related Post
Thank you for visiting our website which covers about What Is Opsec Select All That Apply . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
