Where In A Network Segment Will The Dmz Be Located
Onlines
Mar 22, 2025 · 5 min read
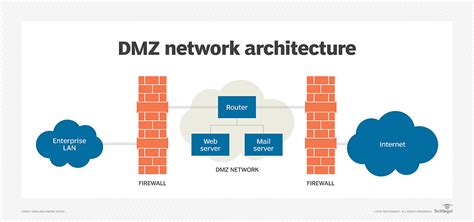
Table of Contents
Where in a Network Segment Will the DMZ Be Located? Demystifying the Demilitarized Zone
The Demilitarized Zone (DMZ) is a critical component of network security, acting as a buffer zone between the public internet and a private internal network. Understanding its placement within a network segment is paramount for effective security architecture. This comprehensive guide will delve into the specifics of DMZ placement, addressing common questions and providing a detailed understanding of its role in protecting your valuable data.
Understanding the Purpose of a DMZ
Before discussing placement, let's solidify the fundamental purpose of a DMZ. Think of it as a controlled access area, a perimeter where publicly accessible servers reside. These servers, such as web servers, mail servers, and FTP servers, need external access but should be isolated from the internal network to prevent breaches. If a hacker compromises a server within the DMZ, they are contained within that segment, preventing access to the more sensitive data residing on your internal network.
Key Functions of a DMZ:
- Protecting Internal Networks: The primary function is to safeguard internal networks from external threats. By isolating public-facing servers, a breach in one area doesn't automatically compromise the entire network.
- Controlled Access: It provides controlled access to specific services, allowing external users to interact with these services without direct access to the internal network.
- Improved Security Posture: Implementing a DMZ significantly enhances the overall security posture of an organization by adding an extra layer of defense.
Strategic Placement of the DMZ within a Network Segment
The ideal location for a DMZ is crucial for its effectiveness. It's typically positioned between the internet and the internal network, acting as a bridge with carefully controlled access points. The exact placement involves a combination of network topology and security considerations.
Typical DMZ Network Architecture:
A common setup uses a three-tier architecture:
- Internet: The external world, encompassing all external networks and potential threats.
- DMZ: The demilitarized zone, housing public-facing servers.
- Internal Network: The private network containing sensitive data and internal servers, accessible only to authorized users.
This architecture utilizes firewalls extensively. One firewall sits between the internet and the DMZ, filtering traffic entering and exiting the DMZ. A second firewall resides between the DMZ and the internal network, protecting the internal network from any compromise within the DMZ. This creates a layered security approach, enhancing protection.
Specific Considerations for DMZ Placement:
- Firewall Configuration: Precise firewall rules are crucial. These rules should strictly control which ports and services are accessible from the internet to the DMZ and from the DMZ to the internal network. Only essential services should be allowed.
- Network Segmentation: Further segmentation within the DMZ itself can be beneficial. This involves dividing the DMZ into smaller, more isolated segments, each housing different services. This limits the impact of a breach, even within the DMZ itself.
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploying IDS/IPS within the DMZ provides an additional layer of security by monitoring network traffic for malicious activity and taking preventative measures.
- Regular Security Audits: Regular security audits and vulnerability assessments are essential to identify and address any potential weaknesses in the DMZ configuration. Keeping software updated is crucial for patching security vulnerabilities.
Alternative DMZ Configurations:
While the three-tier architecture is common, other configurations exist, adapted to specific needs:
Reverse Proxy DMZ:
A reverse proxy server sits within the DMZ, acting as an intermediary between the internet and the internal web servers. This server handles all incoming requests, forwarding only legitimate requests to the internal servers. This adds an extra layer of security by masking the internal server's IP addresses and reducing direct exposure to the internet.
Virtual DMZ:
Virtualization allows for the creation of virtual DMZs, providing greater flexibility and scalability. Virtual machines (VMs) representing public-facing servers can be deployed within a virtual DMZ, providing a secure and isolated environment.
Cloud-Based DMZ:
Cloud providers often offer built-in DMZ capabilities, simplifying the setup and management of a DMZ. They handle the underlying infrastructure, providing security and scalability.
Common Mistakes in DMZ Implementation:
Avoiding these common errors is critical for a secure and effective DMZ:
- Overly Permissive Firewall Rules: Allowing unnecessary services or ports can create significant vulnerabilities. Follow the principle of least privilege—only allow strictly necessary access.
- Lack of Segmentation: Failing to segment the DMZ can significantly increase the impact of a compromise. Divide the DMZ into smaller, isolated zones based on service type.
- Neglecting Regular Security Updates: Outdated software is a prime target for attackers. Regular updates are crucial for patching known vulnerabilities.
- Insufficient Monitoring: Without adequate monitoring, breaches may go undetected for extended periods. Implement robust monitoring and logging to detect suspicious activity.
Advanced DMZ Security Measures:
To further strengthen the security of your DMZ, consider these advanced measures:
- Web Application Firewalls (WAFs): WAFs specifically protect web applications from various attacks, such as SQL injection and cross-site scripting (XSS).
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS systems monitor network traffic for malicious activity and can take actions to block or mitigate threats.
- Regular Penetration Testing: Regular penetration testing helps identify vulnerabilities that may have been missed during other security assessments.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing centralized security monitoring and incident response capabilities.
Choosing the Right DMZ Implementation:
The optimal DMZ implementation depends on several factors, including:
- Network Size and Complexity: Larger and more complex networks may require more sophisticated DMZ configurations.
- Security Requirements: The level of security required will dictate the level of protection needed.
- Budget: Implementing advanced security measures can be costly.
- Technical Expertise: Setting up and managing a DMZ requires technical expertise.
Conclusion:
The DMZ is a critical component of a robust network security architecture. Its placement within the network segment requires careful consideration of security best practices, network topology, and the specific needs of the organization. By understanding the principles of DMZ implementation, following security best practices, and implementing advanced security measures, organizations can significantly enhance their network security and protect their valuable data from external threats. Remember, a well-planned and maintained DMZ is a crucial element in minimizing the risk of a successful cyberattack. Regular review and updates are key to its ongoing effectiveness.
Latest Posts
Latest Posts
-
Springboard Algebra 2 Answer Key Pdf
Mar 22, 2025
-
Soluble And Insoluble Salts Lab 15 Answers
Mar 22, 2025
-
Summary Of Chapter 7 In The Giver
Mar 22, 2025
-
Tienes Que Tratar Amablemente A Los Policias
Mar 22, 2025
-
Yo Lavo Los Platos En
Mar 22, 2025
Related Post
Thank you for visiting our website which covers about Where In A Network Segment Will The Dmz Be Located . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
