Which Of The Following Are Identities Check All That Apply
Onlines
Mar 13, 2025 · 5 min read
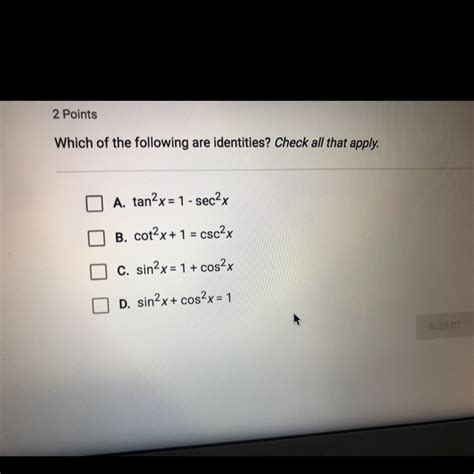
Table of Contents
Which of the following are identities? Check all that apply. A Deep Dive into Identity Verification
The question, "Which of the following are identities? Check all that apply," is deceptively simple. It touches upon a fundamental concept that spans multiple disciplines, from philosophy and psychology to computer science and cybersecurity. Understanding identity, particularly in the context of verification, is crucial in our increasingly digital world. This article will explore the multifaceted nature of identity, examining various aspects and providing a comprehensive guide to identifying what constitutes an identity, especially in the context of verification processes.
What is Identity? A Multifaceted Concept
Before we delve into specific examples, it's essential to define "identity." Identity isn't a singular, easily defined term. Instead, it's a complex construct encompassing several interconnected aspects:
-
Personal Identity: This refers to the unique characteristics that distinguish an individual from others. It encompasses physical attributes (height, weight, eye color), personality traits, beliefs, values, and experiences. This is the identity we most readily associate with ourselves and how we perceive ourselves in relation to the world.
-
Social Identity: This is how we are perceived and categorized by others. It's shaped by our roles within society (student, parent, employee) and group affiliations (nationality, religion, political party). Our social identities significantly influence how we interact with the world and how the world interacts with us.
-
Digital Identity: In the digital age, this is arguably the most rapidly evolving aspect of identity. It refers to the information about an individual that exists online. This can include usernames, passwords, social media profiles, online banking details, and digital footprints left through online activities. Securing and managing one's digital identity is of paramount importance in today's interconnected world.
-
Legal Identity: This refers to the identity established through legal documentation and processes. It includes birth certificates, passports, driver's licenses, and other official documents that verify an individual's name, date of birth, and other legally relevant information. This is crucial for accessing services and rights within a legal framework.
Types of Identity Verification and Their Importance
Understanding different identity verification methods is critical to answering the core question of what constitutes an identity in a verifiable context. These methods are used across various sectors to confirm an individual's identity and prevent fraud or unauthorized access.
-
Knowledge-Based Authentication (KBA): This method relies on personal information known only to the individual, such as their mother's maiden name, date of birth, or previous addresses. While relatively simple to implement, KBA is vulnerable to data breaches and social engineering attacks.
-
Possession-Based Authentication: This involves possessing a physical or digital item that proves identity, such as a passport, driver's license, or a security token. This method is more secure than KBA, but physical items can be lost or stolen.
-
Inherence-Based Authentication (Biometrics): This utilizes unique biological characteristics for identification, such as fingerprints, facial recognition, iris scans, or voice recognition. Biometrics offers a high level of security, but raises concerns about privacy and data security.
-
Multi-Factor Authentication (MFA): This combines two or more of the above methods to enhance security. For example, MFA might require a password (knowledge-based), a security code sent to a mobile phone (possession-based), and fingerprint verification (inherence-based). MFA is considered the most secure approach to identity verification.
Examples of Identities and Verification Methods
Let's consider several examples to illustrate the nuances of identity and its verification:
Scenario 1: Applying for a driver's license.
To obtain a driver's license, you need to prove your legal identity. This typically involves providing documents like a birth certificate, proof of address, and potentially Social Security number. The process uses possession-based authentication (documents) and potentially knowledge-based authentication (answers to security questions).
Scenario 2: Accessing your online banking account.
Accessing your online banking requires verifying your digital identity. This is commonly achieved through a username and password (knowledge-based), possibly combined with a one-time password (OTP) sent to your phone (possession-based), or biometric authentication (inherence-based).
Scenario 3: Creating a social media account.
Creating a social media account often involves providing personal information such as name, email address, and date of birth. While not rigorous identity verification, it establishes a digital identity, albeit a less secure one.
Scenario 4: Verifying your identity for a government service.
Accessing certain government services may require more stringent identity verification. This might involve in-person verification with official documents and potentially biometric scans, utilizing a combination of possession-based and inherence-based authentication methods.
Challenges in Identity Verification
Several challenges complicate identity verification:
-
Data breaches and identity theft: Stolen personal information can be used to impersonate individuals and gain unauthorized access to accounts or services.
-
Evolving technologies: Keeping up with emerging technologies, such as deepfakes and sophisticated AI-powered attacks, is crucial for maintaining robust identity verification systems.
-
Privacy concerns: The use of biometric data and other sensitive information raises ethical and legal concerns about privacy and data protection.
-
Accessibility: Identity verification systems must be accessible to all individuals, regardless of their technological literacy or physical abilities.
The Future of Identity Verification
The future of identity verification will likely involve:
-
Decentralized identity systems: These systems empower individuals to control their own data and share it selectively with organizations.
-
Increased use of biometrics: Biometric authentication is expected to become increasingly prevalent, though concerns about privacy and security need to be carefully addressed.
-
Artificial Intelligence (AI) and machine learning: AI and machine learning can help improve the accuracy and efficiency of identity verification systems, while also helping to detect fraudulent activities.
-
Blockchain technology: Blockchain can provide a secure and transparent way to manage and verify identities.
Conclusion: Defining and Verifying Identity
Determining which of a list of items are identities requires careful consideration of the various aspects of identity: personal, social, digital, and legal. Verification methods employ knowledge, possession, and inherence-based approaches, often combined using multi-factor authentication for enhanced security. Understanding the complexities of identity verification is crucial in navigating the digital landscape and safeguarding personal information in an increasingly interconnected world. The ongoing evolution of technology continues to shape the methods and challenges involved in verifying identities. The focus should be on secure, ethical, and accessible systems that protect individual rights while also preventing fraud and unauthorized access. The question of "which of the following are identities" has no simple checklist; rather, it requires a nuanced understanding of the context and the methods used to validate claims of identity.
Latest Posts
Latest Posts
-
El Futbol En Europa Es Muy Similar Al Futbol Americano
Mar 14, 2025
-
Sinners In The Hands Of An Angry God Quotes
Mar 14, 2025
-
At Kairas Caribbean Cuisine Kaira Improves Focuses On Efficiency By
Mar 14, 2025
-
Of Paramount Significance In The Tabernacle Was The
Mar 14, 2025
-
A Properly Written Statement Of Work Will
Mar 14, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Are Identities Check All That Apply . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
