Which Of The Following Is The Microsoft Version Of Eap
Onlines
Mar 29, 2025 · 6 min read
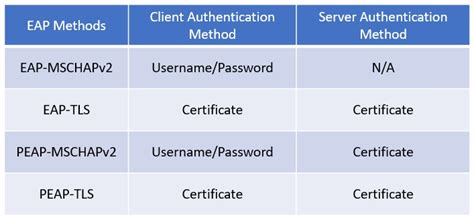
Table of Contents
Which of the following is the Microsoft version of EAP? Understanding Extensible Authentication Protocol and its Microsoft Equivalent
The question "Which of the following is the Microsoft version of EAP?" requires clarification. EAP, or Extensible Authentication Protocol, isn't a single protocol but rather a framework. It allows for various authentication methods to be plugged in, creating a flexible system for verifying user identities. Therefore, there isn't one single "Microsoft version" but rather several Microsoft-developed or supported EAP methods. This article will delve into the intricacies of EAP, explore the common authentication methods within the EAP framework, and specifically highlight those associated with Microsoft.
Understanding Extensible Authentication Protocol (EAP)
EAP is a widely used authentication framework that sits at the heart of many secure network connections. It acts as a tunnel, securely transporting authentication data between a supplicant (your device) and an authenticator (your network access point). This tunnel protects sensitive information, like passwords, from eavesdropping. The key strength of EAP lies in its extensibility: new authentication methods can be added without modifying the core protocol itself. This adaptability is crucial in today's constantly evolving security landscape.
How EAP Works: A Simplified Explanation
Imagine you're trying to access a Wi-Fi network. The process typically follows these steps:
- Connection Initiation: Your device initiates a connection to the Wi-Fi network.
- EAP Negotiation: The network and your device negotiate which EAP method to use. This is like agreeing on a language for communication.
- Authentication Exchange: The chosen EAP method dictates the authentication process. This might involve exchanging credentials, certificates, or using biometrics.
- Authentication Verification: The authenticator verifies your credentials.
- Connection Establishment: If authentication is successful, the connection is established.
This seemingly simple process involves complex security mechanisms to ensure only authorized users can access the network.
The Importance of EAP Security
EAP's strength lies in its ability to support a wide range of security mechanisms. This means it can adapt to various security needs and environments. Using strong encryption and authentication methods, EAP protects against several threats, including:
- Eavesdropping: The secure tunnel prevents unauthorized access to authentication data.
- Man-in-the-middle attacks: EAP's robust authentication methods make it difficult for attackers to intercept and manipulate authentication data.
- Credential theft: By employing strong encryption and secure protocols, EAP helps protect user credentials from theft.
Common EAP Methods
Numerous EAP methods exist, each with its own strengths and weaknesses. Choosing the right method depends on factors like security requirements, infrastructure capabilities, and user experience. Some popular EAP methods include:
- EAP-TLS (Transport Layer Security): This method uses digital certificates for authentication, providing a high level of security. It's often used in enterprise environments with robust PKI (Public Key Infrastructure).
- EAP-TTLS (Tunneled Transport Layer Security): EAP-TTLS offers a compromise between security and simplicity. It uses TLS to protect the password exchange, making it suitable for environments where deploying full certificates is challenging.
- PEAP (Protected EAP): PEAP provides a secure tunnel for transporting other EAP methods, improving security, especially for less secure EAP methods. It often uses TLS to create this secure tunnel.
- EAP-FAST (Flexible Authentication via Secure Tunneling): Developed by Cisco, EAP-FAST offers strong security and simpler certificate management compared to EAP-TLS.
- EAP-SIM (Subscriber Identity Module): Used primarily for mobile devices, EAP-SIM leverages the SIM card for authentication.
- EAP-AKA (Authentication and Key Agreement): A common method used in 3GPP networks, such as those used by mobile carriers.
Microsoft's Role in EAP: Proprietary and Supported Methods
Microsoft plays a significant role in the EAP ecosystem, both by supporting various standard EAP methods and developing its own. While they don't have a single "Microsoft version" of EAP, several methods are closely tied to their technologies and infrastructure.
1. EAP-TLS and Microsoft's Active Directory Integration
Microsoft strongly supports EAP-TLS, integrating it seamlessly with Active Directory. This makes it a popular choice for enterprise networks using Windows-based systems. The combination of Active Directory's robust certificate management and EAP-TLS's high security makes for a powerful authentication solution. Implementing EAP-TLS with Active Directory involves configuring certificate templates and deploying certificates to users and devices. This setup provides strong mutual authentication, ensuring both the client and server can verify each other's identity.
2. PEAP with Microsoft Challenge-Handshake Authentication Protocol (CHAP)
Microsoft also champions PEAP, often used with MS-CHAP v2. This combination provides a robust authentication method suitable for scenarios where certificate deployment is more challenging. PEAP creates a secure tunnel (usually TLS) encapsulating the inner authentication method (MS-CHAP v2). MS-CHAP v2 is a password-based authentication protocol offering better security than older CHAP versions. This combination is commonly used in corporate Wi-Fi networks and VPN connections, balancing security and ease of deployment.
3. Other Microsoft Integrations and Considerations
Microsoft's involvement in EAP extends beyond these specific methods. Their operating systems, networking technologies, and enterprise solutions provide extensive support for various EAP methods, enabling seamless integration within their ecosystem. They often provide tools and utilities to simplify the configuration and management of EAP authentication within their enterprise environments. For instance, Microsoft's Network Policy Server (NPS) plays a crucial role in managing and enforcing EAP authentication policies within a corporate network.
Choosing the Right EAP Method for Your Needs
The "best" EAP method depends entirely on your specific needs and constraints. Factors to consider include:
- Security Requirements: High-security environments might require EAP-TLS, while less stringent environments could opt for PEAP or EAP-TTLS.
- Infrastructure: The availability of a PKI infrastructure is crucial for methods like EAP-TLS.
- Client Devices: Ensure the chosen method is compatible with all client devices that need to access the network.
- Management Complexity: Some methods, like EAP-TLS, require more complex certificate management.
Conclusion: No Single "Microsoft EAP," but Strong Microsoft Support
There's no single Microsoft-branded EAP method. Instead, Microsoft actively supports and integrates several standard EAP methods, offering comprehensive solutions for various security needs and environments. EAP-TLS and PEAP with MS-CHAP v2 are particularly prevalent in Microsoft-centric environments, offering excellent security and integration with Active Directory. Understanding the different EAP methods and their compatibility with your infrastructure is essential when securing your network. Selecting the appropriate method requires careful consideration of your security requirements, existing infrastructure, and the capabilities of your client devices. By carefully evaluating these factors, you can choose the most effective and efficient EAP method for your specific network environment, ensuring robust security and optimal user experience.
Latest Posts
Latest Posts
-
Which Drive Is Displayed First In The Command Window
Mar 31, 2025
-
Which Of The Following Diagrams Involves A Virtual Image
Mar 31, 2025
-
Which Of The Following Statements About Gerrymandering Is True
Mar 31, 2025
-
9 08 Quiz Act 3 Session 3
Mar 31, 2025
-
An Addendum To An Electronic Health Record Ehr Is A
Mar 31, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Is The Microsoft Version Of Eap . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
