Which Of The Following Security Functions Does Chap Perform
Onlines
Apr 01, 2025 · 6 min read
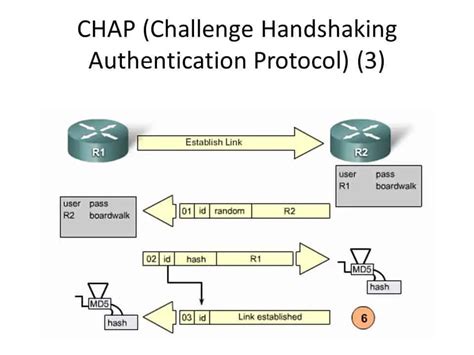
Table of Contents
Which Security Functions Does CHAP Perform?
The world of network security is complex, filled with acronyms and protocols that can be confusing even for experienced professionals. One such protocol is CHAP, or Challenge-Handshake Authentication Protocol. Understanding its role and function is crucial for anyone involved in securing network infrastructure. This article delves deep into CHAP, explaining its core security functions, how it differs from PAP (Password Authentication Protocol), and its strengths and weaknesses.
Understanding CHAP's Core Function: Authentication
At its heart, CHAP's primary security function is authentication. This means verifying the identity of a user or device attempting to access a network resource. Unlike its simpler predecessor, PAP, CHAP doesn't transmit passwords in plain text, making it significantly more secure against eavesdropping attacks.
How CHAP Works: A Step-by-Step Breakdown
CHAP operates through a continuous three-way handshake process, offering ongoing authentication throughout the connection's lifespan:
-
Challenge: The authenticating server (typically a network access server or NAS) sends a random challenge to the client (e.g., a modem or computer). This challenge is a unique, unpredictable string of characters.
-
Response: The client uses a secret shared key (a password or a more sophisticated cryptographic key) to encrypt the challenge. This encrypted response is then sent back to the server.
-
Verification: The server performs the same encryption process using the same shared secret. If the server's calculated response matches the response received from the client, authentication is successful. If there's a mismatch, the connection is denied.
This process isn't a one-time event. The server periodically sends new challenges to the client to maintain continuous authentication, ensuring that the client remains authorized throughout the connection. This continuous verification significantly improves security by detecting compromised clients or compromised shared secrets.
CHAP vs. PAP: A Critical Comparison
CHAP is a significant upgrade over the older PAP protocol. Understanding their differences highlights CHAP's enhanced security features:
| Feature | CHAP | PAP |
|---|---|---|
| Password Transmission | Never transmits passwords in clear text | Transmits passwords in clear text |
| Authentication | Continuous authentication | One-time authentication at connection |
| Security | Highly secure against eavesdropping | Highly vulnerable to eavesdropping |
| Complexity | More complex to implement | Simpler to implement |
| Overhead | Slightly higher overhead | Lower overhead |
As the table shows, PAP's glaring weakness lies in its transmission of passwords in plain text. A malicious actor intercepting the communication can easily obtain the password, compromising the entire system. CHAP, by contrast, significantly mitigates this risk.
Security Features Offered by CHAP
CHAP offers several key security features that enhance network protection:
-
Mutual Authentication: Although less common, CHAP can be configured for mutual authentication, meaning the server authenticates to the client as well. This adds another layer of security, preventing attacks where a malicious server pretends to be a legitimate one.
-
Strong Encryption: The encryption employed by CHAP, while not explicitly specified in the protocol itself (it's implementation-dependent), typically uses strong cryptographic algorithms to protect the challenge-response exchange. This protects against unauthorized access even if the communication is intercepted.
-
Detection of Compromised Clients: The continuous authentication nature of CHAP allows for the detection of compromised clients. If a client's secret key is compromised, the server will fail the authentication process during subsequent challenges.
-
Resistance to Replay Attacks: Because each challenge is unique and time-sensitive, CHAP is resistant to replay attacks, where an attacker attempts to reuse a captured authentication response.
Limitations and Vulnerabilities of CHAP
While CHAP offers considerable security improvements over PAP, it's not without its limitations:
-
Shared Secret Management: The security of CHAP relies heavily on the secure management of the shared secret (password or key) between the client and server. Compromised shared secrets render the authentication mechanism useless. Robust password management practices and secure key exchange mechanisms are crucial.
-
Vulnerability to Denial-of-Service Attacks: A determined attacker can potentially launch denial-of-service (DoS) attacks by flooding the server with authentication requests. While not directly compromising the authentication process itself, this can disrupt legitimate access to the network.
-
No Built-in Encryption for Data Transmission: CHAP only secures the authentication process. It doesn't encrypt the actual data transmitted after authentication. Secure data transmission requires additional protocols like SSL/TLS or IPSec.
-
Implementation Variations: The specific cryptographic algorithms and implementation details of CHAP can vary across different vendors and systems, potentially introducing inconsistencies and vulnerabilities.
Implementing CHAP Securely: Best Practices
To maximize the security provided by CHAP, consider these best practices:
-
Strong Passwords: Use long, complex, and unique passwords for each client. Avoid easily guessable passwords or passwords reused across multiple systems.
-
Regular Password Changes: Implement a policy for regular password changes to minimize the window of vulnerability if a password is somehow compromised.
-
Secure Key Exchange: If using cryptographic keys instead of passwords, ensure a secure key exchange mechanism is employed to prevent interception of the keys during initial setup.
-
Firewall Protection: Protect the network access server and clients using firewalls to prevent unauthorized access and mitigate DoS attacks.
-
Regular Security Audits: Perform regular security audits to identify and address potential vulnerabilities in the implementation of CHAP and related security mechanisms.
-
Consider Stronger Alternatives: While CHAP is a significant improvement over PAP, modern networks often employ more robust authentication protocols like EAP (Extensible Authentication Protocol) which offer greater flexibility and stronger security features. EAP can incorporate various authentication methods, including strong cryptographic mechanisms, providing a more comprehensive solution.
CHAP in the Larger Security Ecosystem
CHAP is frequently used in conjunction with other security protocols and technologies to create a multi-layered security approach. For instance, CHAP is often used with Point-to-Point Protocol (PPP) to secure dial-up or leased line connections. However, as mentioned earlier, CHAP only secures the authentication; securing the actual data transmission usually requires additional layers of security like encryption protocols.
Conclusion: CHAP's Role in Modern Networks
While CHAP offers a significant improvement in security over its predecessor PAP, it's crucial to understand its limitations and vulnerabilities. Its continuous authentication feature provides a strong defense against many attacks but is not a silver bullet solution. In modern network security architecture, CHAP often acts as a component within a broader security strategy, working alongside other protocols and technologies to build a robust and secure network infrastructure. While its use might be declining in favor of more modern and flexible protocols like EAP, understanding CHAP's functions and limitations remains essential for network administrators and security professionals. The principles of secure password management, regular updates, and a layered security approach remain paramount in any network security architecture, regardless of the specific protocols employed.
Latest Posts
Latest Posts
-
Change Management And Patient Advocacy Shadow Health
Apr 02, 2025
-
A Good Witness Is Someone Who Is In Their Thoughts
Apr 02, 2025
-
Exercise 13 Review Sheet Art Labeling Activity 2
Apr 02, 2025
-
Interventions Based On Antecedent Manipulations Act Upon The
Apr 02, 2025
-
When Giving Abdominal Thrusts How Should Brianna Position Her Hands
Apr 02, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Security Functions Does Chap Perform . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
