Wireshark Lab Ip V8 1 Solution
Onlines
Mar 24, 2025 · 7 min read
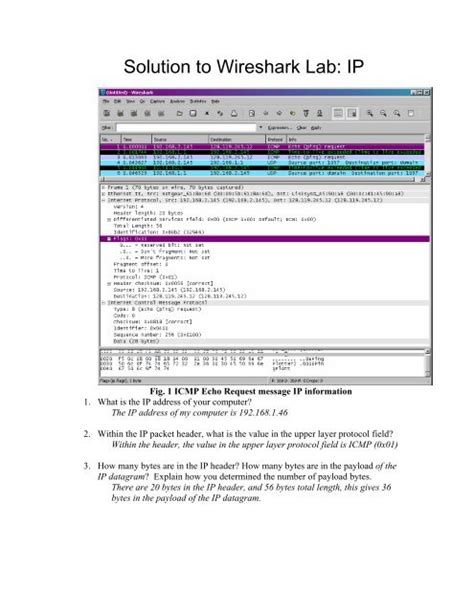
Table of Contents
Wireshark Lab: IPv8 (1) Solution - A Deep Dive into Network Packet Analysis
This comprehensive guide provides a detailed solution to a hypothetical Wireshark lab focusing on IPv8 (understanding that IPv8 is not an existing standard, we'll use this as a framework to explore advanced packet analysis concepts applicable to real-world IPv4 and IPv6 scenarios). The lab will involve analyzing captured network traffic to identify various network behaviors, troubleshoot connectivity issues, and understand the fundamental principles of network communication. We'll dissect specific packet fields and interpret their significance in diagnosing network problems.
Understanding the Hypothetical IPv8 Scenario
For the purpose of this lab, let's imagine IPv8 is a next-generation internet protocol. While it doesn't exist, this allows us to explore advanced concepts that build upon the existing knowledge of IPv4 and IPv6. We will assume IPv8 packets retain some familiar fields, while incorporating new features to reflect future network challenges. These might include:
- Enhanced security features: Think of integrated encryption or authentication mechanisms directly within the header.
- Advanced Quality of Service (QoS): More granular control over traffic prioritization and resource allocation.
- Improved congestion control: New algorithms to optimize network throughput and minimize packet loss.
- Support for extremely large address spaces: Addressing the potential future need for a significantly expanded address space.
These features will manifest in new or modified fields within the hypothetical IPv8 packet header. Our analysis will focus on interpreting these fields and their impact on network communication.
Lab Setup and Data Capture
Before we dive into the analysis, let's assume the lab involves capturing network traffic using Wireshark on a device within the network. We'll need a sample capture file (.pcap or .pcapng) containing various IPv8 packets representing different network activities (e.g., web browsing, file transfers, VoIP calls). For this tutorial, we will describe the expected observations and analysis steps. You would perform these steps on your own captured file.
Analyzing the Hypothetical IPv8 Packets with Wireshark
Our focus will be on using Wireshark's features to analyze the captured traffic, using the hypothetical IPv8 features to showcase real-world analysis techniques:
1. Identifying IPv8 Packets
First, we need to filter the captured traffic to isolate IPv8 packets. In a real scenario, this would involve identifying a specific protocol field or value in the packet header that uniquely identifies IPv8. For the sake of this lab, let's assume we filter using a display filter like: ip.proto == 150 (assuming '150' is the assigned protocol number for IPv8).
2. Examining the IPv8 Header
The IPv8 header will contain various fields, some analogous to IPv4/IPv6 headers, and some unique to the hypothetical protocol. A typical analysis might involve:
- Version: This field will identify the packet as IPv8 (e.g., version 8).
- Traffic Class: This might be a more sophisticated QoS field compared to IPv4's differentiated services (DiffServ) field. We need to analyze its value to understand the packet's priority.
- Flow Label: A field for identifying related packets within a flow, crucial for QoS and congestion control. Analyzing this helps understand the application and its performance.
- Hop Limit: Similar to IPv6's hop limit, this field indicates the maximum number of routers the packet can traverse.
- Source and Destination Addresses: These fields would use IPv8's large address space. Analyzing them helps identify communication endpoints.
- Payload Length: The size of the data carried within the packet.
- Next Header: Indicates the protocol encapsulated within the IPv8 packet (e.g., TCP, UDP, etc.).
- Authentication/Integrity Checksum: Analyzing this field determines if there was any tampering or corruption during transmission (related to our hypothetical enhanced security).
Example Analysis: Let's say we observe a high number of IPv8 packets with a specific Traffic Class value indicating low priority. This could suggest a potential QoS issue where low-priority traffic is being delayed or dropped.
3. Investigating Encapsulated Protocols (TCP/UDP)
Once we've identified the IPv8 packets, we need to examine the protocols carried within their payload (likely TCP or UDP). This will involve:
- Source and Destination Ports: Identify the applications involved in the communication. For example, port 80 indicates HTTP traffic.
- Sequence and Acknowledgement Numbers (TCP): Analyze TCP's three-way handshake and the flow of data. Identify any packet loss or retransmissions, indicative of network congestion or errors.
- Checksums (TCP/UDP): Verify the integrity of the TCP/UDP segments. Errors here suggest transmission issues.
- Flags (TCP): Examine the flags (SYN, ACK, FIN, RST, etc.) to understand the state of the TCP connection.
Example Analysis: Let's say we see frequent TCP retransmissions. This suggests packet loss, which we'd need to investigate further by examining the Hop Limit and the network path.
4. Analyzing Network Performance Metrics
Wireshark provides several tools for analyzing network performance:
- Statistics: Wireshark's statistics feature allows us to analyze packet counts, bytes transferred, and other metrics for different protocols. This provides a high-level overview of network activity.
- Conversation Analysis: Analyzing conversations (between two endpoints) helps pinpoint communication issues. This identifies bottlenecks or dropped packets in specific interactions.
- Time Analysis: Examine the timestamps on packets to determine delays and identify potential latency issues.
Example Analysis: A significant increase in packet loss over time suggests a network problem that needs immediate attention. This analysis might involve checking the network infrastructure for errors or bottlenecks.
5. Troubleshooting Connectivity Issues
Based on the analysis, we can identify and troubleshoot connectivity issues:
- Packet Loss: Examine the reasons for packet loss. Is it due to congestion, network errors, or faulty network equipment?
- High Latency: Identify the points in the network path that are causing high latency. This might require examining the hop limit and investigating individual routers/switches.
- Security Issues: If security features are present in IPv8, analyze any errors or anomalies related to authentication or encryption to identify potential security breaches.
Advanced Analysis Techniques in Wireshark
Beyond the basic steps, we can leverage Wireshark's advanced capabilities:
- Follow TCP Stream: Reconstruct the entire conversation (data exchanged) between two endpoints.
- Expert Information: Use Wireshark's expert information to identify potential problems automatically.
- Coloring Rules: Define custom coloring rules to highlight specific packets based on criteria (e.g., color packets with high latency red).
- Protocol Decoding: Wireshark provides deep protocol decoding which helps understand the application-level details of the communication, enabling more in-depth analysis.
Real-World Application of IPv8 (Hypothetical) Analysis Techniques
Although IPv8 is hypothetical, the techniques applied are directly transferable to analyzing real-world network traffic, especially for IPv4 and IPv6:
- Troubleshooting network connectivity: The process of identifying packet loss, high latency, and other anomalies is identical for IPv4, IPv6, and our hypothetical IPv8.
- Analyzing network security: Examining security-related fields (even if not as integrated as our hypothetical IPv8) helps identify intrusions or vulnerabilities.
- Optimizing network performance: Analyzing QoS parameters, identifying congestion points, and improving routing can be adapted irrespective of the specific IP version.
- Debugging application-level issues: Examining TCP/UDP segments and application-level data allows us to resolve issues in applications relying on network communication.
By applying these techniques, you can effectively troubleshoot and analyze network issues across various protocols. Remember to use filtering, protocol decoding, and performance analysis tools effectively within Wireshark for more in-depth investigation.
Conclusion: Mastering Network Packet Analysis with Wireshark
This in-depth exploration of a hypothetical IPv8 lab, using Wireshark, provides a solid foundation for analyzing network traffic. By understanding packet structures, interpreting field values, and leveraging Wireshark’s powerful analysis tools, you can confidently tackle network troubleshooting, performance optimization, and security assessments. The core principles and techniques discussed remain relevant regardless of the specific IP version in use. Continuous practice and exploration of Wireshark's capabilities are essential for mastering network packet analysis and ensuring smooth, secure, and high-performing network environments. Remember, understanding network protocols is crucial for effective troubleshooting and building a robust network infrastructure.
Latest Posts
Latest Posts
-
Annotations For The Cask Of Amontillado
Mar 29, 2025
-
Relations And Functions Practice 2 1
Mar 29, 2025
-
Semester 2 Exam Spanish 2 Edgenuity
Mar 29, 2025
-
Name The Strong Transparent Covering That Encases The Kidney
Mar 29, 2025
-
Gina Wilson All Things Algebra Unit 2 Homework 7
Mar 29, 2025
Related Post
Thank you for visiting our website which covers about Wireshark Lab Ip V8 1 Solution . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
