An Investigator Obtains Consent And Hipaa
Onlines
Mar 20, 2025 · 6 min read
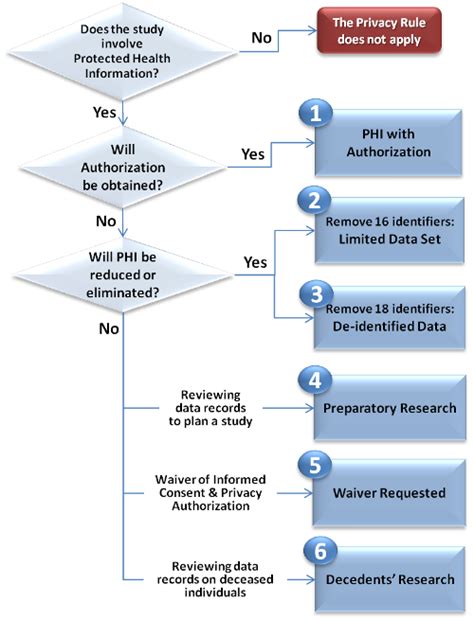
Table of Contents
An Investigator Obtaining Consent and HIPAA Compliance: A Comprehensive Guide
Navigating the complex landscape of research ethics and patient privacy, especially concerning HIPAA (Health Insurance Portability and Accountability Act) compliance, is crucial for any investigator. This guide provides a comprehensive overview of obtaining informed consent and ensuring HIPAA adherence throughout the research process. Failure to comply can lead to significant legal repercussions, reputational damage, and a halt to the research project.
Understanding HIPAA and its Relevance to Research
The HIPAA Privacy Rule protects the privacy and security of Protected Health Information (PHI). PHI includes any individually identifiable health information held or transmitted by a covered entity or its business associate, in any form or media, whether electronic, paper, or oral. This includes, but isn't limited to, medical records, billing information, and even seemingly innocuous details like a patient's name and date of birth.
Covered entities under HIPAA include healthcare providers, health plans, and healthcare clearinghouses. Business associates are individuals or organizations that perform certain functions or activities that involve the use or disclosure of PHI on behalf of covered entities. Research involving PHI often falls under this category.
For researchers, understanding what constitutes PHI is critical. Even seemingly anonymous data might become identifiable if linked to other datasets or if contextual information is revealed. This necessitates robust de-identification strategies and careful data management practices.
Informed Consent: The Cornerstone of Ethical Research
Informed consent is a fundamental ethical principle that ensures individuals voluntarily participate in research after being fully informed about the study's purpose, procedures, risks, and benefits. This process is not merely a formality; it's a crucial step in establishing trust and respecting the autonomy of participants. It also forms a vital aspect of HIPAA compliance, as obtaining informed consent is a crucial element in the permitted use and disclosure of PHI.
Key Elements of an Informed Consent Form:
- Purpose of the research: A clear and concise explanation of the study's goals and objectives.
- Procedures: A detailed description of the research activities the participant will undergo, including data collection methods.
- Risks and discomforts: A thorough assessment of potential physical, psychological, social, or economic risks associated with participation.
- Benefits: A realistic explanation of potential benefits to the participant or to society as a whole. It's crucial to avoid exaggerating or promising benefits that are unlikely.
- Alternatives: A description of alternative treatments or approaches available to the participant.
- Confidentiality: A clear statement regarding how participant data will be protected and maintained confidential. This should explicitly address HIPAA compliance and data security measures.
- Voluntary participation: Emphasis on the participant's right to withdraw from the study at any time without penalty.
- Compensation: Details regarding any compensation or reimbursement for participation.
- Contact information: The contact information of the principal investigator or study team members.
Obtaining Consent in Different Settings:
- In-person consent: This is the most common method, allowing for direct interaction and clarification of any questions or concerns. The investigator should ensure the participant fully understands the information provided before obtaining their signature.
- Written consent: The signed consent form serves as legal documentation of the participant's agreement to participate. It should be kept securely and in compliance with HIPAA regulations.
- Electronic consent: This method involves obtaining consent using electronic devices, such as tablets or computers. Strict security measures must be in place to protect the electronic consent form and ensure data privacy.
- Verbal consent: In certain limited circumstances, and with appropriate institutional review board (IRB) approval, verbal consent might be acceptable. However, this requires meticulous documentation.
HIPAA Compliance in Research: Key Considerations
Integrating HIPAA compliance into the research process requires meticulous planning and execution. Here are some essential considerations:
1. Privacy Rule Compliance:
- Authorization: For the use and disclosure of PHI for research purposes that are not otherwise permitted under HIPAA, investigators must obtain specific authorization from the participants. This authorization must meet stringent requirements, including clear description of the information to be used and disclosed, the purpose of the research, and the recipients of the information.
- De-identification: To avoid the need for authorization, investigators can de-identify PHI. This involves removing all direct identifiers (e.g., name, address, date of birth, medical record number) and any indirect identifiers that could reasonably be used to identify an individual. The Office for Civil Rights (OCR) provides guidance on de-identification techniques. However, even with de-identification, researchers must still maintain appropriate data security and access controls.
- Minimum Necessary Standard: Covered entities must disclose only the minimum necessary PHI for the purpose of the research. This helps reduce the risk of unauthorized disclosure and protects patient privacy.
- Data Security: Robust data security measures are essential. This involves physical security (secure storage of paper records), technical security (encryption of electronic data), and administrative security (access control policies and procedures).
2. Security Rule Compliance:
- Administrative safeguards: Policies and procedures to manage access to PHI, including training for research personnel.
- Physical safeguards: Controlling access to physical locations where PHI is stored.
- Technical safeguards: Using encryption and access controls to protect electronic PHI.
3. Breach Notification:
- In the event of a breach of unsecured PHI, investigators must comply with HIPAA's breach notification rules. This includes notifying affected individuals, the OCR, and potentially the media, depending on the circumstances.
4. IRB Oversight:
- The IRB plays a crucial role in ensuring the ethical conduct of research involving human subjects, including adherence to HIPAA regulations. Investigators must obtain IRB approval before initiating any research involving PHI.
5. Data Use Agreements:
- If the research involves collaborating with other entities, data use agreements should be established to ensure HIPAA compliance across all parties involved.
Practical Strategies for Ensuring Compliance:
- Develop detailed protocols: Create thorough, step-by-step protocols outlining how PHI will be handled throughout the research process. This should cover data collection, storage, analysis, and disposal.
- Implement strict access controls: Limit access to PHI to only authorized personnel with a legitimate need to know.
- Regular training: Conduct regular training for all research personnel on HIPAA regulations and data security best practices.
- Data encryption: Encrypt all electronic PHI, both at rest and in transit, to protect it from unauthorized access.
- Secure data storage: Utilize secure servers and storage devices to prevent unauthorized access to PHI.
- Data anonymization techniques: Employ robust anonymization techniques to remove or obscure identifiers from data sets, reducing the risk of re-identification.
- Regular audits and reviews: Conduct regular audits and reviews of research protocols and data handling practices to identify any compliance gaps.
- Incident response plan: Develop a comprehensive incident response plan to address potential data breaches or security incidents.
Conclusion: A Proactive Approach to Compliance
Ensuring HIPAA compliance and obtaining informed consent are not mere administrative hurdles; they are ethical imperatives that protect participants' rights and maintain the integrity of research. By following the guidelines outlined in this article, investigators can proactively protect patient privacy, maintain the trust of participants, and contribute to the advancement of knowledge in a responsible and ethical manner. Remember that adherence to these principles is not only a legal requirement but also a moral obligation. A proactive and comprehensive approach to HIPAA compliance and informed consent will not only minimize risks but also enhance the overall quality and credibility of research endeavors. Ongoing vigilance and education are essential for maintaining compliance in this ever-evolving landscape of healthcare regulations and ethical research practices. Consult with legal counsel and your IRB regularly for the most up-to-date guidance and advice to ensure that your research practices remain compliant.
Latest Posts
Latest Posts
-
Esta Guayabera Es Bonita Pero Prefiero
Mar 20, 2025
-
Person Responsible For Paying Attention To The Media
Mar 20, 2025
-
Categorize The Compounds Below As Chiral Or Achiral
Mar 20, 2025
-
Summary Of Water By The Spoonful
Mar 20, 2025
-
The Term Formal Education Is Defined By The Text As
Mar 20, 2025
Related Post
Thank you for visiting our website which covers about An Investigator Obtains Consent And Hipaa . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
