How Are Ip Headers Valuable For Security Analysts During Investigations
Onlines
Mar 31, 2025 · 8 min read
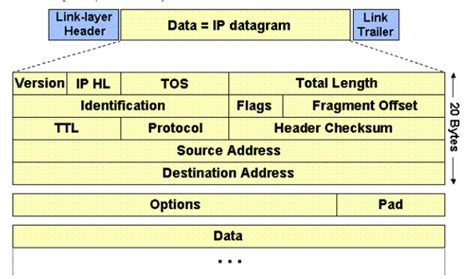
Table of Contents
How IP Headers Are Valuable for Security Analysts During Investigations
IP headers are fundamental to network communication, acting as the address label and control information for every packet traversing the internet. For security analysts, meticulously examining IP headers is crucial during investigations. They provide a wealth of information, acting as digital breadcrumbs that can lead investigators to the source of malicious activity, identify compromised systems, and reconstruct attack timelines. This article will delve into the specific elements within the IP header and explain their significance in security investigations.
Understanding the IP Header Structure
The IP header, while seemingly complex, is a structured collection of fields, each offering unique insights. Let's explore the key fields and their relevance to security analysis:
1. Version (4 bits):
This field simply indicates the IP version (IPv4 or IPv6). While seemingly trivial, knowing the version is vital. Different versions have different header structures and security implications. IPv6, with its larger address space and improved security features, is increasingly prevalent, requiring analysts to adapt their investigative techniques. Detecting a mix of IPv4 and IPv6 traffic in an investigation might highlight unusual activity or a potential breach involving internal network segmentation.
2. Internet Header Length (IHL) (4 bits):
This field specifies the length of the IP header in 32-bit words. Understanding the IHL is critical for parsing the header accurately. Variations from the standard length can indicate header manipulation or fragmentation attempts, which are common tactics in attacks. Any discrepancies should be thoroughly examined.
3. Type of Service (TOS) (8 bits):
The TOS field (now largely superseded by the Differentiated Services Code Point (DSCP) in IPv6) originally indicated priority levels for network traffic. While less frequently used for explicit prioritization now, it can still offer clues. For example, observing unexpectedly high priority assigned to certain traffic during an investigation might raise suspicions about attempts to bypass security controls. Analyzing TOS fields in conjunction with other header elements and network traffic logs will allow for a more complete picture of network usage.
4. Total Length (16 bits):
This field indicates the total length of the entire IP packet, including both the header and the payload data. Analyzing this field helps determine if packets are fragmented, indicating potential evasion techniques used by attackers or network anomalies resulting from routing issues. A fragmented packet might be reassembled during the investigation to reveal the full payload. The size of the packet itself can also be a potential indicator, providing a profile of typical traffic patterns to better detect anomalies.
5. Identification (16 bits):
This field is crucial for fragmented packets. It provides a unique identifier for all fragments belonging to the same original packet. Security analysts use this to reassemble fragmented packets and examine the complete payload, which might otherwise be hidden by fragmentation techniques employed in attacks. This is particularly important in identifying malicious code, which could be spread across fragmented packets.
6. Flags (3 bits):
The flags field contains three bits: Reserved (always 0), Don't Fragment (DF), and More Fragments (MF). The DF bit indicates whether the packet can be fragmented. A set DF bit with subsequent fragmentation signifies a potential issue or an attempt to circumvent fragmentation-based intrusion detection. The MF bit indicates if more fragments follow.
7. Fragment Offset (13 bits):
This field indicates the offset of the current fragment within the original packet. Along with the Identification field, it’s essential for reassembling fragmented packets, which are sometimes used to bypass firewalls or intrusion detection systems (IDS). Analyzing the offset helps understand the order and the reconstruction of the payload.
8. Time to Live (TTL) (8 bits):
The TTL field is a crucial element for security analysis. It represents the maximum number of hops a packet can take before being discarded. Analysts can track the path of a packet by monitoring TTL decay. A low TTL value can indicate a packet originating from a nearby network or a spoofing attempt. Analyzing TTL values helps trace the source of attacks or network anomalies. Unexpectedly long TTL values might point to compromised routers or rogue devices that are artificially keeping packets alive.
9. Protocol (8 bits):
This field identifies the higher-level protocol encapsulated within the IP packet, such as TCP, UDP, or ICMP. Knowing the protocol is essential for further analysis; different protocols have different security characteristics and vulnerabilities. For instance, a UDP packet could be used for DDoS attacks, while a TCP packet may be related to a session hijacking attempt. This information guides further examination of the payload and the context of the communication.
10. Header Checksum (16 bits):
This field is a checksum value that verifies the integrity of the IP header. A corrupted checksum indicates that the header has been altered, potentially by a malicious actor or due to network transmission errors. Detecting inconsistent checksums is a crucial indicator that needs thorough follow-up.
11. Source IP Address (32 bits for IPv4, 128 bits for IPv6):
This field contains the IP address of the sender of the packet. It's a cornerstone of network identification. Analyzing this field allows investigators to identify the source of malicious traffic, trace compromised systems, or pinpoint malicious actors. Investigating this address thoroughly is paramount in determining the extent and origin of any attack.
12. Destination IP Address (32 bits for IPv4, 128 bits for IPv6):
This field indicates the intended recipient of the IP packet. Analyzing destination addresses helps identify targeted systems or servers, helping determine what was being attacked and the extent of the intrusion. Analyzing this field in conjunction with other elements allows security analysts to build a comprehensive picture of network events.
13. Options (Variable Length):
This field is optional and contains various additional options that provide more information. These can include security-relevant data, such as security parameters index (SPI) or other security-related metadata related to IPsec VPNs, making them a valuable source of information in security investigations.
Practical Applications in Security Investigations
Understanding each IP header field allows analysts to perform several crucial security investigation tasks:
-
Tracing Malicious Traffic: By analyzing source and destination IP addresses, TTL values, and potentially the options field, analysts can trace the origin and path of malicious traffic, identifying compromised systems or malicious actors.
-
Identifying Compromised Systems: Examining the source and destination IP addresses in relation to network maps and logs allows analysts to pinpoint potentially compromised systems within their network, even if the infection might seem hidden in other forms.
-
Reconstructing Attack Timelines: Analyzing the timestamps (implicitly associated with packet capture data) and sequence numbers, combined with IP header information, allows analysts to chronologically reconstruct the stages of an attack, aiding in forensic analysis and subsequent mitigation strategies.
-
Detecting Network Anomalies: Deviations from standard traffic patterns or anomalies in IP header fields, such as unexpected fragmentation or unusually high TTL values, can alert analysts to potential attacks or network compromises. Analyzing these anomalies alongside other security data offers better insights and context.
-
Correlating Events: The information within IP headers is often combined with data from other sources, such as firewall logs, intrusion detection system (IDS) alerts, and security information and event management (SIEM) systems, to provide a more complete picture of security incidents.
-
Identifying Spoofing Attempts: Analysts can identify IP address spoofing attempts by comparing source IP addresses with other available information, such as DNS records or internal network maps. Discrepancies can be key indicators of suspicious activity.
-
Analyzing Network Segmentation: Analyzing IP address ranges and the interplay of different protocols within the IP header allows analysts to investigate how well a network is segmented. Breaches in segmentation are often key indicators of successful attacks.
-
Investigating Denial of Service (DoS) Attacks: Analyzing the source IP addresses and volume of packets with similar destination addresses can help identify and quantify a DDoS attack. Monitoring and examining TTL values for unusual behavior can also aid in determining the nature of this attack.
-
Investigating Packet Filtering and Firewall Evasion Techniques: Analysts can detect anomalies caused by specific packet filtering rules or evasion techniques used by attackers. Examining the headers and looking for unexpected fragmentation patterns or unusual header values is crucial.
Tools and Techniques for IP Header Analysis
Several tools and techniques assist security analysts in analyzing IP headers:
-
Packet Capture Tools (Wireshark, tcpdump): These tools capture network traffic and allow analysts to examine the IP headers and payloads of individual packets.
-
Network Monitoring Tools: These tools provide real-time visibility into network traffic, allowing analysts to identify suspicious patterns and potentially malicious activity involving IP headers.
-
Security Information and Event Management (SIEM) Systems: SIEM systems integrate data from various sources, including network devices, and can analyze IP header information to detect threats.
-
Network Forensics Tools: Specialized tools allow detailed analysis of network captures, focusing on identifying anomalies and correlating events within the network.
-
Log Analysis Tools: These tools aid in analyzing security logs and identifying patterns or anomalies related to IP header activity.
Conclusion
The IP header is more than just addressing information; it's a treasure trove of data vital for security analysts. By understanding the structure and meaning of each field, analysts can effectively investigate security incidents, trace malicious activity, identify compromised systems, and build comprehensive timelines of attacks. Proficiency in analyzing IP headers is an essential skill for any security professional involved in incident response and threat analysis. Continuous learning and practice with various tools and techniques are key to mastering this crucial aspect of security investigation. This knowledge empowers analysts to proactively defend against cyber threats and maintain the integrity of their networks.
Latest Posts
Latest Posts
-
If A Generalization Must Be Made It Should
Apr 01, 2025
-
Which Of These Statements About The Elderly Is True
Apr 01, 2025
-
The Bible Itself Has Never Really Faced Extreme Persecution
Apr 01, 2025
-
The Team Functions Smoothly When All Team Members
Apr 01, 2025
-
To Which Patient Might The Nurse Apply A Physical Restraint
Apr 01, 2025
Related Post
Thank you for visiting our website which covers about How Are Ip Headers Valuable For Security Analysts During Investigations . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
