Security Plans Are Not Living Documents True Or False
Onlines
Mar 07, 2025 · 6 min read
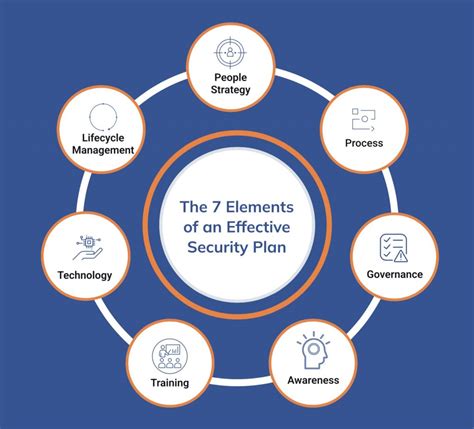
Table of Contents
Security Plans: Living Documents or Static Snapshots? The Truth Unveiled
The statement "security plans are not living documents" is unequivocally false. A robust and effective security plan is, in fact, a dynamic, evolving entity that requires constant attention, adaptation, and revision. Treating it as a static document, filed away and only dusted off during audits, is a recipe for disaster. In today's rapidly changing threat landscape, a stagnant security plan is practically an invitation for breaches. This article delves deep into why security plans must be living, breathing documents, exploring the crucial elements of their ongoing evolution and the consequences of neglecting this essential aspect of cybersecurity.
The Ever-Shifting Landscape of Cybersecurity Threats
The digital world is in constant flux. New vulnerabilities are discovered daily, sophisticated attack vectors emerge, and the tactics employed by malicious actors continuously evolve. Ransomware attacks become more targeted and devastating, phishing schemes become more convincing, and zero-day exploits pop up unexpectedly. A security plan created even six months ago might already be significantly outdated, failing to address the latest threats and vulnerabilities.
Why Static Security Plans Fail:
- Technological advancements: New technologies introduce new vulnerabilities and require updated security protocols. A static plan can't keep up with the rapid pace of technological innovation.
- Evolving threat landscape: Cybercriminals are constantly adapting their techniques. A static plan won't account for newly emerging threats or evolving attack methods.
- Changes in organizational structure: Mergers, acquisitions, departmental restructuring, and even employee turnover can drastically alter the security landscape within an organization. A static plan can't adapt to these organizational changes.
- Regulatory compliance: Regulations and compliance standards are frequently updated. A static plan may quickly become non-compliant, exposing the organization to legal and financial penalties.
- Increased sophistication of attacks: Cyberattacks are becoming more sophisticated and targeted. A static plan, relying on outdated strategies, won't effectively mitigate these advanced threats.
Key Components of a Living Security Plan
A truly "living" security plan isn't merely a document; it's a comprehensive process that integrates several key elements:
1. Regular Reviews and Updates:
This is the cornerstone of a living security plan. Scheduled reviews, ideally quarterly or even monthly, are essential to ensure its continued relevance. These reviews should involve a multidisciplinary team, including IT security professionals, compliance officers, and representatives from various departments. The reviews should assess:
- Effectiveness of existing controls: Are current security measures successfully mitigating threats? Are there any gaps in protection?
- Emerging threats and vulnerabilities: What new threats are emerging, and how can the plan be adapted to address them? Are there any new zero-day exploits to consider?
- Technological changes: Have any significant changes in technology occurred that require updates to the security infrastructure or policies?
- Compliance requirements: Are current policies and procedures still in line with relevant regulations and compliance standards?
- Incident response effectiveness: Analyze past incidents to identify areas for improvement in the incident response plan.
2. Proactive Threat Hunting and Vulnerability Assessments:
A reactive approach, waiting for attacks to happen, is insufficient. A living security plan embraces proactive threat hunting and regular vulnerability assessments. This includes:
- Penetration testing: Simulating real-world attacks to identify weaknesses in the security infrastructure.
- Vulnerability scanning: Regularly scanning systems and applications for known vulnerabilities.
- Security audits: Conducting periodic audits to assess the overall security posture of the organization.
- Threat intelligence: Monitoring threat feeds and staying informed about emerging threats and vulnerabilities.
3. Flexible and Adaptable Structure:
The plan itself shouldn't be a rigid, inflexible document. It should be structured in a way that allows for easy updates and modifications. Consider using a wiki-style platform or a collaborative document management system that enables multiple users to contribute and update the plan simultaneously.
4. Clearly Defined Roles and Responsibilities:
Everyone needs to understand their role in maintaining security. The plan should clearly outline the responsibilities of each individual and team. This includes:
- Security team: Defines the roles and responsibilities of the security team in managing and maintaining the security plan.
- Departmental responsibilities: Outlines specific security responsibilities for each department within the organization.
- Incident response team: Clearly defines the roles and responsibilities of the incident response team during security incidents.
5. Comprehensive Documentation and Training:
A living security plan is not just about the technical aspects; it's about the people too. Comprehensive documentation helps everyone understand the plan's contents and their responsibilities. Regular training sessions should educate employees on security best practices and the importance of their role in maintaining security.
6. Metrics and Reporting:
Track key security metrics to measure the effectiveness of the plan. Regular reporting helps identify areas for improvement and demonstrates the value of the security program to stakeholders.
The Consequences of Neglecting a Living Security Plan
Failing to treat a security plan as a living document has significant consequences:
- Increased vulnerability to attacks: Outdated security measures leave the organization exposed to new and evolving threats.
- Data breaches and financial losses: A breach can lead to significant financial losses, legal liabilities, and reputational damage.
- Non-compliance with regulations: Outdated policies can lead to non-compliance with relevant regulations and significant penalties.
- Loss of customer trust: A data breach can severely damage customer trust and lead to a loss of business.
- Operational disruption: A successful cyberattack can disrupt business operations, leading to lost productivity and revenue.
Real-World Examples of the Importance of Adaptive Security
Consider the rapid evolution of ransomware attacks. What worked to mitigate ransomware a year ago may be completely ineffective against today's more sophisticated variants. Similarly, the rise of AI-powered attacks requires security plans to incorporate AI-driven threat detection and response mechanisms. Organizations that fail to adapt their security plans to these evolving threats are far more likely to suffer a successful attack.
Conclusion: Embracing the Dynamic Nature of Security
The assertion that security plans are not living documents is fundamentally incorrect. In the ever-evolving world of cybersecurity, a static security plan is a liability, not an asset. A robust and effective security posture necessitates a proactive, adaptive, and continuously updated security plan. By integrating the key components discussed above, organizations can create a truly "living" security plan, one that effectively protects against the ever-changing threat landscape and safeguards their valuable assets. Ignoring this dynamic approach invites disaster; embracing it fosters resilience and ensures long-term security. Investing time and resources in creating and maintaining a living security plan is not just good practice; it's essential for survival in today's digital world. The cost of inaction far outweighs the investment in a robust, adaptable security strategy.
Latest Posts
Latest Posts
-
The Physical Setting Chemistry Answer Key
Mar 09, 2025
-
Alicia Is Going To College And Working A Fulltime Job
Mar 09, 2025
-
2 2 Worksheet Part 2 Asl Answers
Mar 09, 2025
-
Single Payer Systems Typically Apply All Of The Following Practices Except
Mar 09, 2025
-
Answer Key Nihss Certification Test Answers
Mar 09, 2025
Related Post
Thank you for visiting our website which covers about Security Plans Are Not Living Documents True Or False . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
