Which Of The Following Best Describes A Honeypot
Onlines
Mar 14, 2025 · 6 min read
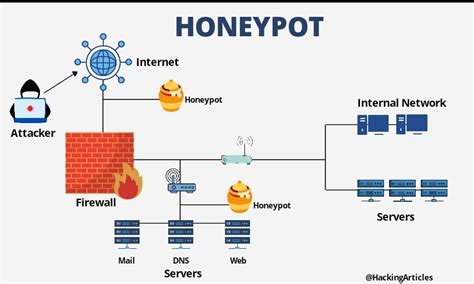
Table of Contents
Which of the Following Best Describes a Honeypot? A Deep Dive into Deception Technologies
The question "Which of the following best describes a honeypot?" isn't easily answered with a single, simple definition. Honeypots are deceptively simple in concept but incredibly nuanced in their implementation and application. Understanding what a honeypot truly is requires delving into its core functionality, various types, and the strategic role it plays within a broader cybersecurity framework. This article will explore honeypots comprehensively, providing a detailed explanation suitable for both cybersecurity novices and experienced professionals.
What is a Honeypot? The Foundation of Deception Technology
At its most basic level, a honeypot is a deceptively attractive system designed to lure and trap attackers. It mimics valuable assets within a network, enticing malicious actors to interact with it. This interaction provides valuable intelligence about attackers' tactics, techniques, and procedures (TTPs), delaying actual attacks, and enriching threat intelligence databases. Think of it as a digital decoy, drawing attackers away from your genuine systems while simultaneously providing crucial information about their methods.
Key Characteristics of a Honeypot:
- Deception: The core principle is deception. Honeypots are designed to appear vulnerable and enticing, tempting attackers to explore and exploit them.
- Data Collection: The primary goal is to collect data about attacker behavior. This includes identifying the tools and techniques they use, their motivations, and their ultimate objectives.
- Limited Functionality: Honeypots are typically low-risk environments with minimal functionality. They should never contain sensitive data, and their limited functionality prevents significant damage if compromised.
- Monitoring: Sophisticated monitoring tools are essential for tracking attacker activity and analyzing the gathered data.
- Low-Impact: A compromised honeypot shouldn't impact the rest of the network. This means it's isolated and closely monitored.
Types of Honeypots: A Spectrum of Deception
Honeypots aren't monolithic; they come in various forms, each serving a specific purpose and offering varying degrees of sophistication. The primary classification is based on the level of interaction allowed:
1. Low-Interaction Honeypots:
These are simpler, pre-configured systems offering limited interaction. They typically present a static environment, responding to common attack attempts with pre-programmed responses. Think of them as highly controlled, simulated systems.
- Advantages: Easy to deploy and manage, requiring less maintenance and resources. They are less likely to be detected as false.
- Disadvantages: Limited data collection capabilities compared to high-interaction honeypots. They might not capture the full scope of an attacker's actions.
2. High-Interaction Honeypots:
These offer a dynamic and interactive environment, allowing for more extensive engagement with attackers. They emulate real systems more accurately, providing a richer dataset on attacker behavior. However, they require more expertise to manage and carry a greater risk of being exploited.
- Advantages: Provides much richer data on attacker techniques and methods. They allow for in-depth analysis of attacker motivations and strategies.
- Disadvantages: Higher risk if compromised; they require more expertise to manage and maintain. They may require more resources for proper monitoring.
Honeypot Deployment Strategies: Location, Location, Location (and Type)
The effectiveness of a honeypot significantly depends on its placement and the type of honeypot employed. Consider these deployment strategies:
- Production Network Deployment: Placing honeypots within the production network provides a realistic environment and allows for real-time monitoring of actual attack attempts. However, this carries the highest risk, necessitating careful planning and security measures.
- DMZ Deployment: Deploying honeypots in a demilitarized zone (DMZ) provides a buffer zone between the public internet and the internal network. This approach minimizes the risk to the internal network but might limit the type of attacks observed.
- Cloud-Based Deployment: Leveraging cloud infrastructure enables scaling and flexibility. This is an increasingly popular approach, providing an easily scalable and cost-effective solution.
- Hybrid Approach: Many organizations utilize a combination of low- and high-interaction honeypots, strategically placed across different parts of their network, offering comprehensive threat intelligence.
Beyond the Basics: Advanced Honeypot Concepts
To fully grasp the scope of honeypot technology, we need to explore some more advanced concepts:
1. Honeynets:
Instead of a single honeypot, a honeynet is a collection of interconnected honeypots, simulating a complete network infrastructure. This approach provides a more realistic environment for attackers and offers a wider range of data collection opportunities. Honeynets are more complex to set up and manage, but offer a more comprehensive view of attacker behaviour.
2. Adaptive Honeypots:
These honeypots dynamically adjust their behavior based on attacker interactions, creating a more realistic and challenging environment. They learn from previous attacks, making them more effective over time. This requires sophisticated AI/ML algorithms for adaptation, increasing their complexity.
3. Virtual Honeypots:
Leveraging virtualization technology, these honeypots can be easily deployed, replicated, and destroyed, offering a flexible and scalable solution. This offers better efficiency in resource utilization and easier deployment in various locations.
4. Sensor-Based Honeypots:
These honeypots focus on collecting data and providing insights without simulating a full system. They act as sensors within the network, detecting and monitoring malicious activity without actively interacting with the attacker. They are often passive systems focusing on detection rather than interaction and deception.
The Ethical Considerations: Responsible Honeypot Deployment
Deploying honeypots responsibly is crucial. Ethical implications must be carefully considered:
- Legal Compliance: Ensure compliance with relevant laws and regulations concerning data collection and network security.
- Informed Consent: If honeypots are used to gather information about individuals, informed consent might be required. This is less relevant for general security monitoring but crucial if personal information is involved.
- Privacy Concerns: Data collected from honeypots must be handled responsibly, adhering to privacy regulations. Anonymization and secure storage practices are critical.
- Transparency: Being transparent about the use of honeypots within an organization's security posture is important, particularly for compliance and legal reasons.
Analyzing Honeypot Data: Turning Insights into Action
The data gathered from honeypots is invaluable for threat intelligence. Analyzing this data allows for:
- Identifying Attack Vectors: Understanding how attackers attempt to compromise systems.
- Detecting Zero-Day Exploits: Identifying new vulnerabilities that haven't been publicly disclosed.
- Improving Security Measures: Using the insights to strengthen security posture and defenses.
- Developing Threat Models: Building more effective threat models based on real-world attacker behavior.
- Enhancing Incident Response: Using data to improve incident response procedures and efficiency.
Conclusion: Honeypots—A Vital Component of Modern Cybersecurity
Honeypots are a powerful tool in the cybersecurity arsenal. They offer a proactive approach to security, allowing for the collection of valuable threat intelligence and improving an organization's overall security posture. Understanding the different types, deployment strategies, and ethical considerations associated with honeypots is crucial for effectively leveraging this deception technology. By combining various types of honeypots, implementing appropriate monitoring, and responsibly analyzing collected data, organizations can significantly enhance their ability to detect, understand, and respond to cyber threats. The ongoing evolution of honeypot technology, particularly with the integration of AI and machine learning, promises even more sophisticated and effective deception strategies in the future. Therefore, staying informed about advancements in this field is paramount for maintaining a robust cybersecurity strategy.
Latest Posts
Latest Posts
-
Amoeba Sisters Video Recap Pedigrees Answer Key
Mar 14, 2025
-
1 The Five Common Types Of Expressway Interchanges Are
Mar 14, 2025
-
What Is The Authors Viewpoint In This Excerpt
Mar 14, 2025
-
Po Box 115009 Carrollton Tx 75011
Mar 14, 2025
-
Topic 1 Performance Assessment Form A Answers
Mar 14, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Best Describes A Honeypot . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
