12.6.6 Check Your Understanding - Wlan Threats
Onlines
Mar 16, 2025 · 7 min read
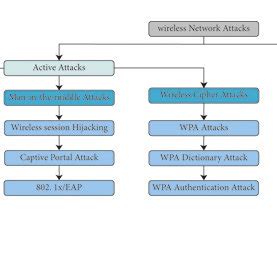
Table of Contents
12.6.6 Check Your Understanding: WLAN Threats – A Comprehensive Guide
Wireless Local Area Networks (WLANs), while offering incredible convenience and flexibility, are unfortunately vulnerable to a wide range of security threats. Understanding these threats is crucial for implementing effective security measures and protecting your network and data. This comprehensive guide delves into the most prevalent WLAN threats, exploring their mechanisms, potential impact, and mitigation strategies.
Common WLAN Threats: A Detailed Breakdown
WLAN security is a multifaceted challenge, and neglecting any aspect can leave your network exposed. Let's examine some of the most significant threats:
1. Rogue Access Points (RAPs): Unauthorized Entry Points
Rogue access points are unauthorized wireless access points installed within a network without the knowledge or consent of the network administrator. These can be intentionally malicious (e.g., to gain unauthorized access) or unintentionally installed (e.g., an employee setting up a personal access point). RAPs represent a significant security risk because they bypass network security controls, creating vulnerabilities for:
- Data breaches: Sensitive data transmitted through the rogue AP is easily intercepted.
- Network infiltration: Attackers can use RAPs to gain access to the internal network and launch further attacks.
- Denial of service (DoS): A rogue AP can overload the network, disrupting legitimate users.
- Man-in-the-middle (MitM) attacks: Attackers can position themselves between legitimate users and the network, intercepting and manipulating communications.
Mitigation: Effective mitigation strategies include robust network monitoring, regular security audits, and the implementation of strong access control policies. Using network discovery tools can help identify unauthorized access points.
2. Evil Twin Attacks: Spoofing Legitimate Access Points
Evil twin attacks involve setting up a fraudulent wireless access point with a similar name (SSID) to a legitimate access point. Users unknowingly connect to the malicious AP, allowing the attacker to:
- Intercept data: All data transmitted through the evil twin is visible to the attacker.
- Launch phishing attacks: The attacker can redirect users to fake websites to steal credentials.
- Install malware: Malicious software can be injected into the user's device through the connection.
Mitigation: Educating users about the risks of connecting to unknown networks is critical. Verifying the legitimacy of an access point before connecting, checking for valid security certificates (like SSL/TLS), and using strong passwords can significantly reduce the risk.
3. Wireless Denial of Service (DoS) Attacks: Disrupting Network Availability
Wireless DoS attacks aim to overwhelm the WLAN with excessive traffic, rendering it unusable for legitimate users. This can be achieved through various techniques, such as:
- Flooding: Overwhelming the access point with a large number of connection requests.
- Spoofing: Sending forged packets to disrupt network operations.
- Jamming: Using devices to interfere with the wireless signal.
Mitigation: Implementing robust Quality of Service (QoS) policies, using intrusion detection/prevention systems (IDS/IPS), and employing strong authentication mechanisms can help mitigate DoS attacks. Regular network capacity planning and upgrades are also crucial.
4. Man-in-the-Middle (MitM) Attacks: Intercepting Network Traffic
MitM attacks involve an attacker intercepting communication between two parties. In the context of WLANs, this can occur through various methods, including:
- Evil twin attacks (as discussed above): The attacker creates a fraudulent access point to intercept traffic.
- ARP poisoning: The attacker manipulates the Address Resolution Protocol (ARP) to redirect network traffic.
- DNS spoofing: The attacker redirects DNS requests to a malicious server.
Mitigation: Using strong encryption protocols (like WPA3), implementing network segmentation, and deploying firewalls can significantly reduce the risk of MitM attacks. Regular security audits and employee training are also important.
5. Wireless Network Intrusion: Unauthorized Access
Wireless network intrusion involves unauthorized access to the WLAN. This can occur through various vulnerabilities, including:
- Weak security protocols: Using outdated or weak encryption protocols like WEP makes the network vulnerable to cracking.
- Default passwords: Failing to change default passwords on routers and access points creates an easy entry point.
- Poor access control: Lack of proper authentication and authorization mechanisms allows unauthorized access.
Mitigation: Using strong encryption protocols (WPA2/WPA3), implementing strong password policies, and regularly updating firmware are crucial. Regular security audits and employing intrusion detection systems can help identify and prevent intrusions.
6. Bluetooth Attacks: Exploiting Bluetooth Connectivity
While not directly related to WLAN, Bluetooth devices can be exploited to gain access to a network or steal data. Attackers can use techniques like:
- Bluejacking: Sending unsolicited messages to Bluetooth-enabled devices.
- Bluesnarfing: Accessing data on a Bluetooth-enabled device without authorization.
- Bluebugging: Taking complete control of a Bluetooth-enabled device.
Mitigation: Disabling Bluetooth when not in use, using strong pairing codes, and keeping Bluetooth devices updated with security patches are recommended.
7. Wardriving: Identifying Vulnerable Networks
Wardriving involves driving around with a wireless-enabled device to identify open or weakly secured wireless networks. This information can be used to access these networks without authorization.
Mitigation: Using strong encryption protocols, configuring strong passwords, and employing access control lists (ACLs) can prevent wardriving from succeeding.
8. MAC Address Spoofing: Disguising Device Identities
MAC address spoofing involves changing the Media Access Control (MAC) address of a device to gain unauthorized access to a network that uses MAC address filtering for access control.
Mitigation: Using more robust authentication methods, such as WPA2/WPA3, which are not easily bypassed by MAC address spoofing, is the best defense. Dynamic IP address allocation can also mitigate some of the risks associated with MAC address spoofing.
9. Session Hijacking: Taking Over User Sessions
Session hijacking involves an attacker stealing a user's session ID to gain unauthorized access to the network.
Mitigation: Using HTTPS for all web traffic, employing robust session management techniques, and implementing regular security audits are recommended.
10. Wireless Phishing: Deceiving Users for Information
Wireless phishing is similar to traditional phishing but targets users connected to a WLAN. The attacker might create a fake login page or send malicious emails, aiming to steal credentials.
Mitigation: Educating users about phishing techniques, verifying website security before entering credentials (look for "https" and security certificates), and using strong and unique passwords for each account are crucial steps to prevent wireless phishing attacks.
11. Data Breaches: Exposing Sensitive Information
Data breaches on WLANs can result from any of the vulnerabilities discussed above. Sensitive data like customer information, financial records, and intellectual property can be exposed to attackers.
Mitigation: Implementing strong encryption, access control, and data loss prevention (DLP) measures is critical to minimize the risk of data breaches. Regular security audits and employee training can also reduce the probability of data breaches.
12. Malware Infections: Compromising Devices
Malware infections can occur through various methods, such as malicious websites, infected email attachments, or compromised software. Infected devices can then be used to launch further attacks or steal data.
Mitigation: Installing and regularly updating antivirus and anti-malware software, keeping operating systems and applications updated with security patches, and educating users about safe browsing habits are key steps to prevent malware infections.
Implementing Effective WLAN Security: A Multi-Layered Approach
Effective WLAN security requires a multi-layered approach that combines various security measures. The following strategies are crucial:
-
Strong Authentication and Authorization: Implement robust authentication protocols like WPA2/WPA3 to protect against unauthorized access. Employ strong passwords and regularly change them.
-
Encryption: Use strong encryption protocols like WPA3 to secure data transmitted over the wireless network.
-
Access Control Lists (ACLs): Control access to the WLAN by specifying which devices are allowed to connect.
-
Network Segmentation: Divide the network into smaller segments to limit the impact of security breaches.
-
Intrusion Detection/Prevention Systems (IDS/IPS): Monitor network traffic for malicious activity and take action to prevent attacks.
-
Regular Security Audits: Conduct regular security audits to identify vulnerabilities and weaknesses in the network.
-
Firmware Updates: Keep all network devices updated with the latest firmware to patch security vulnerabilities.
-
Employee Training: Educate employees about WLAN security threats and best practices to prevent security incidents.
-
Network Monitoring: Continuously monitor the network for suspicious activity, such as unauthorized access attempts or unusual traffic patterns.
Conclusion: Proactive Security is Key
The threats to WLAN security are constantly evolving, requiring a proactive and adaptable security strategy. By implementing robust security measures and staying informed about the latest threats, organizations and individuals can significantly reduce their risk of security breaches and protect their valuable data. Remember, a multi-layered approach, coupled with regular security audits and employee training, is crucial for maintaining a secure and reliable WLAN. Neglecting these precautions can expose your network to significant vulnerabilities and potentially devastating consequences.
Latest Posts
Latest Posts
-
All Flags Such As Porn And Upsetting Offensive Are Query Independent
Mar 17, 2025
-
An Electrical Motor Provides 0 50 W Of Mechanical Power
Mar 17, 2025
-
Studying Marketing Should Help You To Blank
Mar 17, 2025
-
Shaping Clay On A Rapidly Turning Wheel Is Called
Mar 17, 2025
-
During The International Coronavirus Pandemic Many People
Mar 17, 2025
Related Post
Thank you for visiting our website which covers about 12.6.6 Check Your Understanding - Wlan Threats . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
