14.9.10 Packet Tracer - Implement Stp Security
Onlines
Mar 17, 2025 · 5 min read
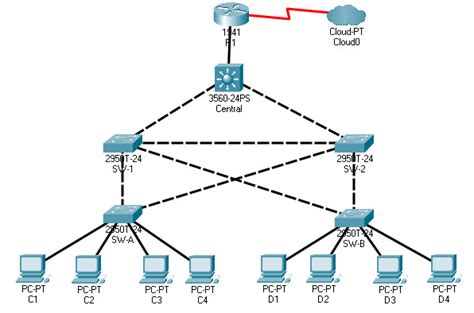
Table of Contents
14.9.10 Packet Tracer: Implementing STP Security – A Comprehensive Guide
Spanning Tree Protocol (STP) is a crucial networking protocol that prevents bridging loops, ensuring network stability and avoiding broadcast storms. However, even with STP implemented, networks can still be vulnerable. This article delves deep into the Packet Tracer 14.9.10 activity focusing on implementing STP security measures, covering various aspects from basic configuration to advanced security considerations. We will explore the importance of STP, its potential vulnerabilities, and how to mitigate them using best practices and advanced techniques.
Understanding the Vulnerability of STP
While STP is essential for network stability, it's not inherently immune to security threats. The core vulnerability lies in the fact that STP relies on exchanging BPDUs (Bridge Protocol Data Units) between switches. Malicious actors could potentially manipulate these BPDUs to disrupt network operations. Here's a breakdown of the primary risks:
Root Bridge Attacks:
A malicious switch could attempt to become the root bridge, potentially disrupting the spanning tree and causing network outages or performance degradation. This is achieved by manipulating the Bridge Priority and MAC address within the configuration. A lower bridge priority value makes a switch more likely to become the root bridge.
BPDU Guard:
This feature is crucial to mitigating root bridge attacks. When enabled on a port, BPDU Guard immediately shuts down the port if it receives a BPDU. This prevents unauthorized switches from interfering with the established spanning tree topology. It's crucial to correctly configure BPDU Guard on edge ports (ports connecting to end devices, not other switches). Accidental configuration on an internal port could disrupt legitimate STP operations.
BPDU Filter:
This feature filters BPDUs from being sent or received on a port. This is typically configured on edge ports, preventing them from participating in the STP process and further enhancing security. However, it also means that the port won't participate in the spanning-tree calculation, so this should be carefully configured and monitored.
Root Guard:
This feature prevents a port from becoming a root port. This is effective in securing a specific branch of the network. By designating a port as edge and then activating Root Guard on that port, you prevent any other switch from becoming the root bridge within that specific network segment. It is mainly implemented in preventing the election of undesirable switches as the root bridge.
PortFast:
This feature accelerates the convergence of STP by placing edge ports directly into the forwarding state without going through the listening and learning states. While not directly a security feature, PortFast improves network availability, reducing the window of vulnerability during STP convergence. However, incorrect use can compromise STP’s function, causing a bridging loop. It should be used only on edge ports, which are directly connected to end devices.
Implementing STP Security in Packet Tracer 14.9.10
Let's delve into the practical implementation of STP security within Packet Tracer 14.9.10. We'll use a sample network scenario, demonstrating the steps involved.
Scenario: Protecting a Corporate Network
Imagine a corporate network with three switches (Switch1, Switch2, Switch3) and several end devices (PCs, servers). Switch1 is the core switch. Switch2 and Switch3 are connected to Switch1 and have various edge ports connected to end devices.
Steps:
-
Configure Basic STP: First, ensure STP is enabled on all switches. This is usually enabled by default, but it's vital to verify the configuration.
-
Identify Edge Ports: Carefully identify all edge ports on Switch2 and Switch3, i.e., ports connected directly to end devices (PCs, servers, etc.). These are the ports that need the additional STP security configurations.
-
Configure BPDU Guard: On all identified edge ports on Switch2 and Switch3, enable BPDU Guard. This prevents unauthorized switches from manipulating the STP topology through those ports. The command is typically
spanning-tree portfast bpduguard enable. -
Configure BPDU Filter (Optional): As an added layer of security, you can enable BPDU Filter on these edge ports. This prevents the ports from even receiving BPDUs, offering further protection against malicious attacks. The command is generally
spanning-tree portfast bpdufilter enable. Note that this method might not always be the most appropriate method as it requires additional configuration and might not always be compatible with all STP implementations. -
Configure Root Guard (Optional): This is useful to protect the connection between the core switch (Switch1) and the other switches (Switch2 and Switch3). Enabling Root Guard prevents Switch2 or Switch3 from becoming the root bridge for their respective network segments. This is very beneficial, especially in network scenarios where the core switch needs to be the root bridge.
-
Configure PortFast (with caution): On the same edge ports, enable PortFast. This ensures faster network convergence after a topology change. Remember, misuse of PortFast can lead to bridging loops if not correctly implemented on edge ports only.
-
Verify Configuration: After implementing these security measures, meticulously verify the configuration on each switch using the appropriate commands (e.g.,
show spanning-tree,show spanning-tree detail) to ensure the settings are applied correctly.
Advanced Security Considerations:
-
Regular Monitoring: Regularly monitor your network for any unusual STP activity. Tools within Packet Tracer can help visualize the STP topology, and inconsistencies could indicate a potential attack.
-
Access Control Lists (ACLs): ACLs can be used to restrict access to switch management interfaces, preventing unauthorized configuration changes that could affect STP.
-
Strong Authentication: Employ strong passwords and authentication mechanisms to prevent unauthorized access to your switches.
-
Regular Firmware Updates: Keeping your network equipment's firmware up-to-date is crucial for patching any known security vulnerabilities.
Conclusion
Implementing STP security is a multi-layered approach requiring a thorough understanding of the protocol and its potential vulnerabilities. This guide provided a practical walkthrough using Packet Tracer 14.9.10, demonstrating how to configure BPDU Guard, BPDU Filter, Root Guard, and PortFast effectively. Remember that the correct placement and implementation of these security features are crucial. Incorrect placement can render your network vulnerable and compromise the functionality of STP. Combining these techniques with robust monitoring and access control practices creates a significantly more secure and resilient network. Always remember that security is an ongoing process requiring continuous vigilance and adaptation to emerging threats. Regular audits and updates to your security policies are crucial to maintaining the security of your network.
Latest Posts
Latest Posts
-
All Flags Such As Porn And Upsetting Offensive Are Query Independent
Mar 17, 2025
-
An Electrical Motor Provides 0 50 W Of Mechanical Power
Mar 17, 2025
-
Studying Marketing Should Help You To Blank
Mar 17, 2025
-
Shaping Clay On A Rapidly Turning Wheel Is Called
Mar 17, 2025
-
During The International Coronavirus Pandemic Many People
Mar 17, 2025
Related Post
Thank you for visiting our website which covers about 14.9.10 Packet Tracer - Implement Stp Security . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
