Simulation Lab 13.1 Module 13 Using Discretionary Access Control
Onlines
Mar 15, 2025 · 5 min read
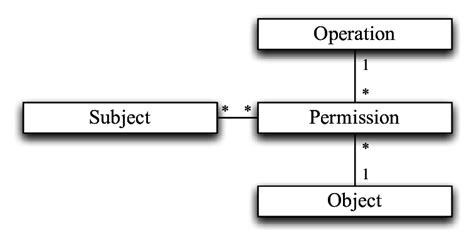
Table of Contents
Simulation Lab 13.1: Module 13 – Mastering Discretionary Access Control
This comprehensive guide delves into Simulation Lab 13.1, focusing on Module 13 and the crucial concept of Discretionary Access Control (DAC). We'll explore the intricacies of DAC, its implementation within the simulation, and how to effectively manage permissions and access rights. This detailed walkthrough will equip you with the practical skills to confidently navigate this challenging module.
Understanding Discretionary Access Control (DAC)
Discretionary Access Control is a fundamental security mechanism that grants the owner of a resource (file, folder, etc.) the authority to dictate who can access it and what actions they can perform. Unlike other access control models, DAC doesn't rely on pre-defined rules or central administration. Instead, the owner has complete control, allowing for flexibility but potentially introducing security risks if not managed properly.
Key Characteristics of DAC:
- Owner Control: The owner of a resource holds ultimate authority over its access permissions.
- Flexibility: Offers granular control, allowing owners to tailor permissions based on specific needs.
- Potential Risks: Improper management can lead to security vulnerabilities, as owners may inadvertently grant excessive access or fail to revoke permissions.
- Implementation: Commonly implemented through Access Control Lists (ACLs), which define permissions for each user or group.
DAC vs. Other Access Control Models
It’s important to understand DAC in the context of other access control models:
- Mandatory Access Control (MAC): A stricter model where access is determined by predefined security labels and clearance levels, independent of the resource owner's wishes. This is often used in high-security environments.
- Role-Based Access Control (RBAC): Focuses on assigning permissions based on roles within an organization. This is a more structured and manageable approach compared to DAC.
- Attribute-Based Access Control (ABAC): A sophisticated model utilizing attributes of users, resources, and the environment to determine access, offering fine-grained control and scalability.
While DAC offers flexibility, its inherent risks often lead organizations to utilize a hybrid approach, combining DAC with elements of other models to enhance security.
Navigating Simulation Lab 13.1: Module 13
Simulation Lab 13.1, Module 13, provides a hands-on experience in implementing and managing DAC. The specific tasks within the lab likely involve scenarios where you'll need to:
- Create Users and Groups: Setting up user accounts and groups to represent different individuals and teams within a simulated environment.
- Create Files and Folders: Establishing the resources that will be subject to access control.
- Assign Permissions using ACLs: The core of the lab, where you'll assign Read, Write, and Execute permissions to various users and groups for specific files and folders.
- Modify Permissions: Changing existing permissions to adjust access rights as needed.
- Revoke Permissions: Removing access rights from users or groups, a critical aspect of maintaining security.
- Troubleshooting Access Issues: Identifying and resolving problems that may arise due to incorrect permission settings.
Step-by-Step Walkthrough (Hypothetical Scenario)
Since the exact details of the simulation are not provided, let's create a hypothetical scenario and walkthrough based on typical DAC concepts within a simulation environment:
Scenario: We're simulating a small company with three users: john (administrator), jane (employee), and bob (employee). We have two folders: projectA and projectB.
Steps:
-
User and Group Creation: Create users
john,jane, andbob. Optionally, you could create a group,employees, and addjaneandbobto it. -
Folder Creation: Create the
projectAandprojectBfolders. -
Initial Permissions:
projectA: Grantjohnfull control (read, write, execute). Grantjaneread and write access. Denybobaccess.projectB: Grantjohnfull control. Grant theemployeesgroup read access.
-
Testing Access: Attempt to access both folders as each user. Verify that permissions are correctly enforced.
johnshould have full access to both.janeshould have read/write access toprojectAand read access toprojectB.bobshould have no access. -
Permission Modification: Let's say
janeneeds write access toprojectB. Modify the permissions forprojectBto grantjanewrite access. Retest access. -
Permission Revocation: If
janeleaves the company, you'll revoke her access to both folders. This is a vital security practice. Retest access. -
Advanced Scenarios (Potential Lab Tasks):
- Inheritance: Explore how permissions inherit down the directory structure. If a folder has specific permissions, subfolders might inherit those unless explicitly overridden.
- Special Permissions: Some simulations may include advanced permissions like "change" or "ownership." Experiment with these to understand their effects.
- ACL Manipulation: The lab likely involves direct manipulation of ACLs, perhaps using command-line tools or a graphical interface provided by the simulation. Familiarize yourself with the specific commands and methods required.
Security Implications and Best Practices
While DAC's flexibility is attractive, it necessitates careful management to avoid security vulnerabilities. Improper configuration can lead to:
- Data Breaches: Unintentional sharing of sensitive information due to excessive permissions.
- Unauthorized Modifications: Malicious actors gaining write access and altering critical data.
- Denial of Service (DoS): Overly permissive settings potentially causing resource exhaustion.
Best Practices for Implementing DAC:
- Principle of Least Privilege: Grant only the minimum necessary permissions to users and groups. Avoid granting excessive access.
- Regular Auditing: Periodically review and audit access permissions to ensure they remain appropriate.
- Separation of Duties: Distribute responsibilities across multiple individuals to prevent any single person from having excessive control.
- Strong Password Policies: Implement robust password policies to protect user accounts from unauthorized access.
- Regular Updates and Patching: Keep the operating system and security software updated to address known vulnerabilities.
- Careful User Management: Employ strict processes for adding, modifying, and removing users and groups.
- Documentation: Maintain thorough documentation of the access control policies and permissions.
Conclusion: Mastering DAC in Simulation Lab 13.1
Simulation Lab 13.1, Module 13, offers invaluable experience in implementing and managing Discretionary Access Control. By understanding the nuances of DAC, its security implications, and best practices, you'll be well-equipped to navigate the lab's challenges and develop strong security skills. Remember to thoroughly document your steps, meticulously test your configurations, and prioritize secure practices to ensure the integrity of your simulated environment. Through careful execution and a keen awareness of potential risks, you can effectively master the concepts of DAC and build a foundation for more advanced security studies. This hands-on experience will prove invaluable in your understanding of real-world access control challenges.
Latest Posts
Latest Posts
-
One Source Of Lead On Some Job Sites Is
Mar 17, 2025
-
When Responding To Litigation Holds Foia Requests Investigations Or Inquiries
Mar 17, 2025
-
Participant Motivation Is Usually The Result Of
Mar 17, 2025
-
All Flags Such As Porn And Upsetting Offensive Are Query Independent
Mar 17, 2025
-
An Electrical Motor Provides 0 50 W Of Mechanical Power
Mar 17, 2025
Related Post
Thank you for visiting our website which covers about Simulation Lab 13.1 Module 13 Using Discretionary Access Control . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
