Quiz: Module 11 Security In Network Design
Onlines
Mar 29, 2025 · 7 min read
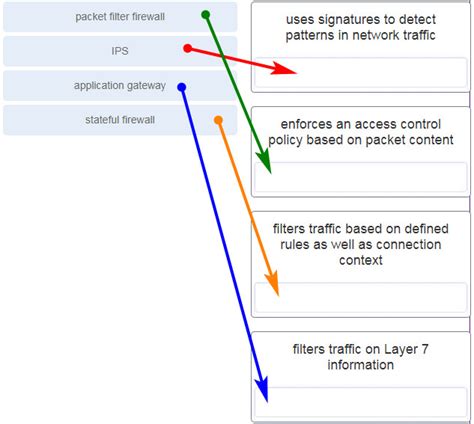
Table of Contents
Quiz: Module 11 Security in Network Design: A Comprehensive Guide
This comprehensive guide delves into the key concepts of network security within the context of Module 11, providing in-depth explanations and practical examples to solidify your understanding. We'll cover crucial security measures, potential threats, and best practices for designing secure networks. This guide acts as a robust resource, exceeding the scope of a typical quiz, to ensure you grasp the intricacies of network security.
Understanding the Fundamentals of Network Security
Before diving into specific security measures, it's crucial to establish a firm understanding of fundamental security concepts within network design. This foundational knowledge forms the bedrock for effective security implementation.
Confidentiality, Integrity, and Availability (CIA Triad)
The CIA triad represents the core principles of information security:
-
Confidentiality: Ensuring that sensitive data is accessible only to authorized individuals or systems. This involves measures like encryption, access control lists (ACLs), and strong authentication mechanisms. Breaches of confidentiality can lead to data leaks and identity theft.
-
Integrity: Guaranteeing the accuracy and completeness of data and preventing unauthorized modifications. Hashing algorithms, digital signatures, and version control systems are vital for maintaining data integrity. Compromised integrity can result in inaccurate information leading to flawed decisions.
-
Availability: Ensuring that authorized users have timely and reliable access to information and resources. This involves redundancy, failover mechanisms, and disaster recovery planning. Unavailability can cripple operations and lead to significant financial losses.
Threat Modeling and Risk Assessment
Proactive security begins with identifying potential threats and assessing their associated risks. Threat modeling involves systematically identifying vulnerabilities and potential attack vectors within a network design. Risk assessment then analyzes the likelihood and impact of these threats, enabling prioritization of security measures.
-
Common Threats: Denial-of-service (DoS) attacks, malware infections, man-in-the-middle (MitM) attacks, unauthorized access, and data breaches are just some of the threats a network faces.
-
Risk Assessment Factors: Consider the likelihood of a threat occurring, the potential impact of a successful attack, and the cost of implementing security controls.
Implementing Security Measures in Network Design
Effective network security is a multifaceted approach, requiring a combination of strategies and technologies. Let's explore key security measures to integrate into your network design.
Firewalls
Firewalls act as the first line of defense, filtering network traffic based on predefined rules. They inspect incoming and outgoing packets, blocking malicious traffic while allowing legitimate communication.
-
Types of Firewalls: Packet filtering firewalls, stateful inspection firewalls, application-level gateways (proxies), and next-generation firewalls (NGFWs) offer varying levels of security. NGFWs, in particular, offer advanced features like intrusion prevention and application control.
-
Firewall Placement: Firewalls should be strategically placed at network boundaries (perimeter firewalls) and within the network (internal firewalls) to segment traffic and enhance security.
Virtual Private Networks (VPNs)
VPNs create secure, encrypted connections over public networks, protecting data transmitted between remote users and the network. VPNs are essential for securing remote access and protecting sensitive data during transit.
-
VPN Protocols: Different VPN protocols (e.g., IPSec, OpenVPN, SSL/TLS) offer varying levels of security and performance. Choosing the appropriate protocol depends on the specific security requirements and network infrastructure.
-
VPN Deployment: VPNs can be deployed as site-to-site connections (connecting two or more networks) or remote access VPNs (allowing individual users to connect securely).
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS systems monitor network traffic for malicious activity. An IDS detects and alerts administrators to suspicious events, while an IPS actively blocks or mitigates threats.
-
Signature-Based Detection: IDS/IPS systems utilize databases of known attack signatures to identify malicious traffic.
-
Anomaly-Based Detection: These systems analyze network traffic patterns to identify deviations from normal behavior, detecting zero-day attacks.
-
Placement: IDS/IPS systems can be deployed inline (IPS) or passively (IDS) to monitor network traffic.
Access Control Lists (ACLs)
ACLs define rules that control network access based on various criteria such as IP addresses, ports, and protocols. They restrict access to sensitive resources, preventing unauthorized users from accessing them.
-
ACL Placement: ACLs can be configured on routers, switches, and firewalls to control network access at various points.
-
Rule Ordering: The order of rules within an ACL is crucial; the first matching rule determines the action taken.
Encryption
Encryption protects data by transforming it into an unreadable format. Only those with the decryption key can access the original data.
-
Symmetric Encryption: Uses the same key for encryption and decryption. Faster but requires secure key exchange.
-
Asymmetric Encryption: Uses separate keys for encryption and decryption (public and private keys). More secure for key exchange but slower.
-
Encryption Protocols: SSL/TLS, IPSec, and SSH are widely used encryption protocols.
Multi-Factor Authentication (MFA)
MFA enhances security by requiring users to provide multiple forms of authentication, such as passwords, tokens, biometrics, or one-time codes. This adds an extra layer of protection, making it more difficult for attackers to gain unauthorized access.
-
MFA Methods: Various MFA methods offer different levels of security and convenience.
-
Implementation: MFA can be implemented at various access points, including VPNs, network devices, and applications.
Designing Secure Networks: Best Practices
Designing a secure network requires a holistic approach encompassing several best practices.
Network Segmentation
Dividing the network into smaller, isolated segments limits the impact of a security breach. If one segment is compromised, the attacker's access is restricted to that segment.
-
VLANs: Virtual LANs (VLANs) are a common method for network segmentation, allowing logical separation of devices without requiring physical changes.
-
Firewalls: Firewalls between segments control traffic flow between them.
Regular Security Audits and Penetration Testing
Regular security audits identify vulnerabilities and ensure compliance with security standards. Penetration testing simulates real-world attacks to uncover weaknesses in the network's defenses.
-
Vulnerability Scanning: Automated tools scan for known vulnerabilities in network devices and software.
-
Ethical Hacking: Experienced security professionals attempt to exploit vulnerabilities to identify weaknesses.
Security Awareness Training
Educating users about security best practices and potential threats is crucial. Training can significantly reduce the risk of human error, a major cause of security incidents.
-
Phishing Awareness: Training users to recognize and avoid phishing attempts.
-
Password Security: Educating users about creating and managing strong passwords.
Patch Management
Keeping software and operating systems up-to-date with the latest security patches is essential for preventing known vulnerabilities from being exploited.
-
Automated Patching: Implementing automated patching systems reduces the risk of human error.
-
Patch Testing: Testing patches in a test environment before deploying them to production systems.
Advanced Security Considerations
Beyond the foundational security measures, several advanced techniques further enhance network security.
Zero Trust Security Model
The zero-trust model assumes no implicit trust, verifying every user and device attempting to access network resources. This approach enhances security by requiring continuous authentication and authorization.
-
Microsegmentation: Dividing the network into extremely small, isolated segments.
-
Continuous Authentication: Regularly verifying user and device identities.
Security Information and Event Management (SIEM)
SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events. This helps detect and respond to security incidents more effectively.
-
Log Aggregation: Collecting logs from various network devices and applications.
-
Security Event Correlation: Identifying relationships between different security events.
Cloud Security
As organizations increasingly adopt cloud services, securing cloud environments becomes crucial.
-
Cloud Access Security Broker (CASB): CASBs control and monitor access to cloud applications.
-
Virtual Private Cloud (VPC): VPcs provide isolated sections within a cloud provider's infrastructure.
Data Loss Prevention (DLP)
DLP tools prevent sensitive data from leaving the network unauthorized. They monitor data in transit and at rest, preventing data breaches.
-
Data Classification: Identifying and classifying sensitive data.
-
Data Monitoring: Tracking data movement to identify potential leaks.
Conclusion: Building a Robust and Secure Network
Building a robust and secure network requires a layered approach, combining multiple security measures and best practices. By understanding the fundamental principles of network security, implementing appropriate security technologies, and continuously monitoring and improving your network's security posture, you can significantly reduce the risk of security breaches and protect your valuable data. This comprehensive guide provides a thorough overview of the key concepts discussed in Module 11, exceeding the typical quiz scope to help you build a strong understanding of network security design principles. Remember, security is an ongoing process—constant vigilance and adaptation are critical in the ever-evolving landscape of cyber threats. Regularly review and update your security measures to stay ahead of emerging threats and maintain a secure network environment.
Latest Posts
Latest Posts
-
Ap Calculus Bc Unit 3 Progress Check Mcq
Apr 01, 2025
-
Which Of These Is False About Lithospheric Plates
Apr 01, 2025
-
1 06 Quiz Sinusoidal Graphs Vertical Shift
Apr 01, 2025
-
An Audit Is Defined By Ich E6 As
Apr 01, 2025
-
4 17 Lab Mad Lib Loops
Apr 01, 2025
Related Post
Thank you for visiting our website which covers about Quiz: Module 11 Security In Network Design . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
